Physical Layer Security for MmWaveCommunications: Challenges and Solutions
HE Miao,LI Xiangman,NI Jianbing
(Department of Electrical and Computer Engineering,Queen’s University,Kingston,Ontario K7L 3N6,Canada)
Abstract: The mmWave communication is a promising technique to enable human commutation and a large number of machine-type communications of massive data from various non-cellphone devices like Internet of Things (IoT) devices,autonomous vehicles and remotely controlled robots.For this reason,information security,in terms of the confidentiality,integrity and availability (CIA),becomes more important in the mmWave communication than ever since.The physical layer security (PLS),which is based on the information theory and focuses on the secrecy capacity of the wiretap channel model,is a cost effective and scalable technique to protect the CIA,compared with the traditional cryptographic techniques.In this paper,the theory foundation of PLS is briefly introduced together with the typical PLS performance metrics secrecy rate and outage probability.Then,the most typical PLS techniques for mmWave are introduced,analyzed and compared,which are classified into three major categories of directional modulation (DM),artificial noise (AN),and directional precoding (DPC).Finally,several mmWave PLS research problems are briefly discussed,including the low-complexity DM weight vector codebook construction,impact of phase shifter (PS) with finite precision on PLS,and DM-based communications for multiple target receivers.
Keywords: mmWave communication;physical layer security;phased array;directional modulation
1 Introduction
The millimeter-wave (mmWave) communication employs high frequencies (30–300 GHz) as the carrier frequencies.With the advantage of high carrier frequencies,mmWave communication has much wider available spectrum than that of sub-6 GHz communication.It can provide high data transmission rates with wide spectrum bandwidths[1].According to the Frequency Range 2 (FR2) defined in the 5G New Radio (NR)[2],the minimum channel spectrum bandwidth defined for FR2 is 50 MHz and the maximum is 400 MHz.With such wide spectrum bandwidths,the mmWave band 5G network can achieve the data transmission rate up to 1.8 Gbit/s[3].In addition,due to the millimeter-level short wave length of mmWave,the physical dimension of antennas for an mmWave communication device can be greatly reduced.Hundreds to thousands of antenna elements can be integrated as a phased array on the device to enable narrow beamforming[4].Therefore,mmWave wireless communication is one of the key technologies in 5G NR for 5G mobile networks[5–6]that can significantly increase the data transmission rate over small and densely populated areas.It is also expected to be applied in the 6G mobile network,which can support the future growing network applications in the Internet of Things (IoT),the Vehicle-to-everything (V2X),etc.[7–8]
Despite the appealing characteristics and applications,the mmWave communications are vulnerable to eavesdropping due to the open nature of the wireless medium[8–10].Eavesdroppers may intercept the communication[10]by residing in the transmitting beam.Such vulnerability threats the confidentiality of some sensitive information,such as financial data,electronic media and medical records.To minimize the risk of sensitive information leakage from mmWave communications,preserving the secrecy is essential in the design and implementation of the mmWave communication system[8,11].
The traditional cryptography technique is an effective tool to protect the information security.However,traditional cryptography techniques can hardly meet the new requirements of the mmWave communication security.First,traditional cryptography techniques are all based on the mathematical computation complex problem and the secret key.Proper key management is essential to ensure the security.The huge device density and highly dynamic environment make it extremely difficult to design a safe key management protocol for traditional cryptography-based security schemes[12–13].Second,traditional cryptography-based algorithms,especially asymmetric cryptography algorithms,require significant computation resource.Many devices in mmWave communication scenarios,especially in the 5G network,are IoT devices.For the reason of cost control,these devices are typically built with very limited computational capabilities in terms of the CPU speed,storage size and power supply.Performing the traditional highcomputation-cost cryptography algorithm on these resource limited devices may not only deteriorate the individual device life span but also result in poor performance[12,14].Lastly,a trusted third party is always required for system initialization and key management in the security scheme based on traditional cryptography.For security reasons,the trusted third party is typically remotely centralized.The dependence on a centralized third party limits the application within a centralized model,which limits the scalability of the mmWave communication,such as the supporting of up to one million devices in per square km[15–16]in 5G networks.And the frequent interactions with the remote party will cause additional delay and increase the system overhead.
Thus,physical layer security (PLS),which is based on the information theory and focuses on the secrecy capacity of the wiretap channel model,gains much attention from academia and industry.While applying to the mmWave communication security,the PLS techniques have significant advantages compared to the traditional cryptography techniques[15,17].First,the PLS technique is based on the information theory fundamentals,instead of computational complexity.It greatly reduces the burden on the devices to run the traditional heavy cryptography algorithms[18].While naturally having good support on lightweight devices with limited computational and power resources,the PLS techniques can still protect the information security in the mmWave communication,even with the existence of powerful computational eavesdroppers[15].Second,the PLS technique does not rely on the centralized trusted third party for system initialization and key management.The future network with mmWave communications may be with highly dynamic access[17],which means that any device may join or leave the network at any time,especially under mobile scenarios with the Internet of Vehicles (IoV) and unmanned aerial vehicles (UAV).The PLS technique can perform secure data transmission or user authentication directly without the time-consuming system setup.It not only significantly lowers the complexity of system management to lower the implementation cost,but also greatly reduces the latency with lower communication overhead.
In this paper,we first give a brief introduction to the theoretical foundation of PLS together with the typical PLS performance metrics secrecy rate and outage probability.Then,we introduce,analyze and compare the typical PLS techniques for mmWave,which are classified into three major categories of directional modulation (DM),artificial noise (AN),and directional precoding (DPC).Several schemes based on these techniques are discussed in detail to reveal each technique’s advantages and constraints in the mmWave environment.Finally,we propose several future mmWave PLS research problems including low-complexity DM weight vector codebook construction,impact of phase shifter (PS) with finite precision on PLS,and DM-based communication for multiple target receivers.The definitions of frequently used acronyms are presented in Table 1.
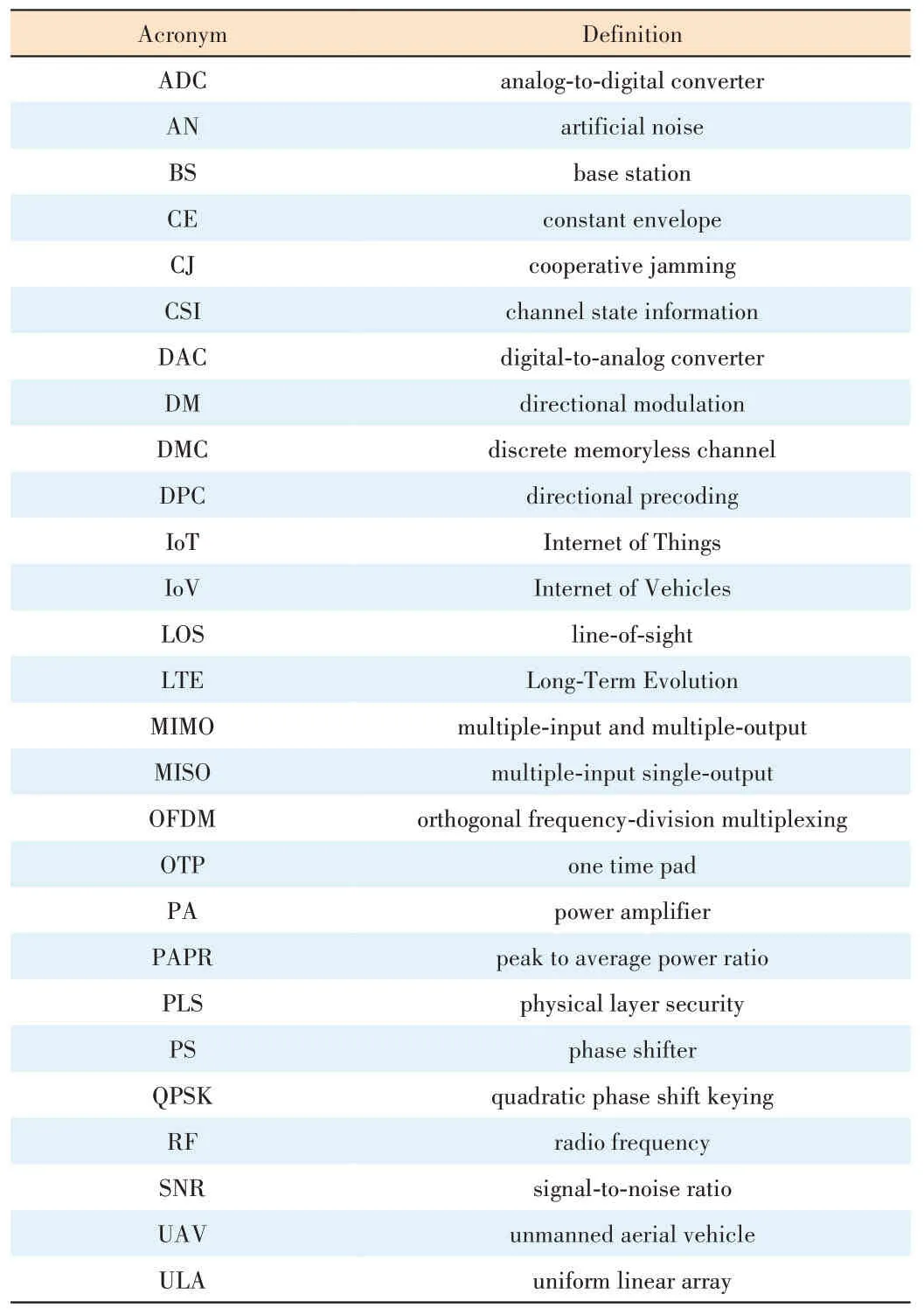
▼Table 1.Summary of Acronyms
2 Theoretical Background for Physical Layer Security
The theoretical foundation of traditional cryptography is the number theory and abstract algebra.Different from traditional cryptography,the theoretical foundation of the PLS technique is the information theory.By minimizing eavesdroppers’ channel capacity with the PLS techniques,information privacy can be preserved at a certain security level.Based on the definition of a channel,the PLS techniques can be classified into two major categories: one is the coding technique aiming at coding channels and the other is the signal processing technique aiming at modulation channels.In this section,we introduce the information theory related concepts in the PLS and review the wiretap channel and several performance evaluation metrics on PLS.
2.1 Perfect Security
Information security has been a topic in human history for thousands of years.The earliest known use of cryptography is found in the wall of a tomb from the Old Kingdom of Egypt circa 1900 BC[18].Until the 1940s,information security in communications was first mathematically analyzed from the view of information theory by Claude Shannon.The concept of information-theoretically secure communication or “perfect security” was also introduced[19].Perfect security means that the ciphertext gives absolutely no additional information about the plaintext.Shannon has proved that perfect security can be achieved with the one-time pad (OTP) even against adversaries with infinite computational power.Perfect security aims to protect the confidentiality of the information.While confidentiality is perfectly protected,integrity and availability can also be protected at a certain level.
2.2 Physical Layer Security
To achieve perfect security in communications from the view of information theory,there are extremely strict restrictions on the OTP.The OTP must be the same size as,or longer than,the message to be sent.The OTP must be pre-shared in a secure channel.The OTP can only be used once.These strong restrictions make perfect security only available to be implemented in very limited applications with extremely high costs.In most communications,the required security level does not have to achieve perfect security.On the other hand,the information security techniques should be scalable and affordable for daily use.For these reasons,an acceptable weaker level of information security known as PLS was defined in the wiretap channel model by WYNER in the 1970s[20].Similar to perfect security,the PLS also focuses on the protection of information confidentiality.
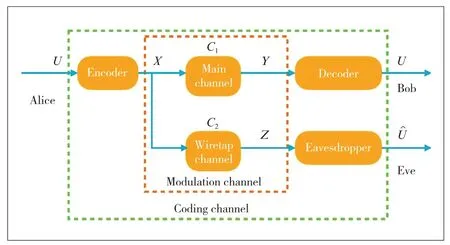
▲Figure 1.Wiretap model
In the wiretap channel model,three parties are defined,as shown in Fig.1.They are Alice,Bob and Eve.Alice wants to send the message with particular information to Bob as private as possible.Eve eavesdrops the message from Alice to Bob and tries to get the information as much as possible.There are two channels in the model.One is between Alice and Bob (legitimate channel).The other is between Alice and Eve (wiretap channel).Due to the randomness of the physical medium (noise,interference,fading,etc.),differences between these two channels exist.The PLS techniques take advantage of these differences to make the channel from Alice to Bob statistically better than that from Alice to Eve.Thus,the channel capacity between Alice and Bob is higher than the wiretap channel between Alice and Eve.If the data rate from Alice is lower than that of the legitimate channel capacity but higher than the wiretap channel capacity,reliable communication could be achieved in the legitimate channel but not in the wiretap channel.In this way,information confidentiality can be preserved between Alice and Bob.
To measure the secrecy of PLS techniques,several performance metrics have been introduced in information theoretic terms.Among all the metrics,secrecy capacity and outage probably are the most accepted.
2.3 Secrecy Capacity
Secrecy capacity characterizes the maximal rate to meet two requirements in wiretap channels.One requirement is that Bob can reliably get the information in the message sent from Alice through legitimate channels.The other requirement is that Eve cannot get any information in the message sent from Alice through wiretap channel.For discrete memoryless channels (DMC),WYNER first introduced the secrecy capacity for the case of degraded channels[20]as
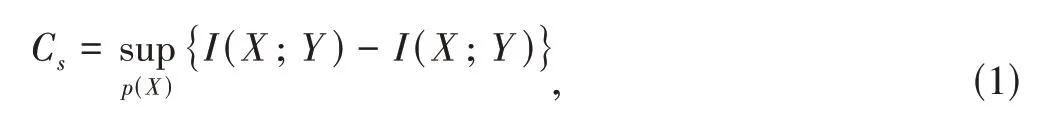
whereXis the input of information source,andYandZare the output of legitimate receiver and eavesdropper,respectively.X,YandZform a Markov chainX→Y→Z.The wiretap channel model for PLS in discrete memoryless channels can be extended to models in wireless channels[21].Gaussian wiretap channel is widely accepted for PLS in wireless channels.It has linear time-invariant multiplicative links with additive white Gaussian noise.Thus,at intervali,the transmitted signal by Alice isXi,and the received signals by Bob and Eve areYB,iandYE,i,respectively.They can be expressed as

HerehBandhEare the channel gains for the legitimate channel and wiretap channel,respectively.NB,iandNE,iare the additive Gaussian noises.They are independent of the transmitted signal with zero means and variancesandrespectively.With the average transmit power constraint ofP,the secrecy capacity can be expressed as
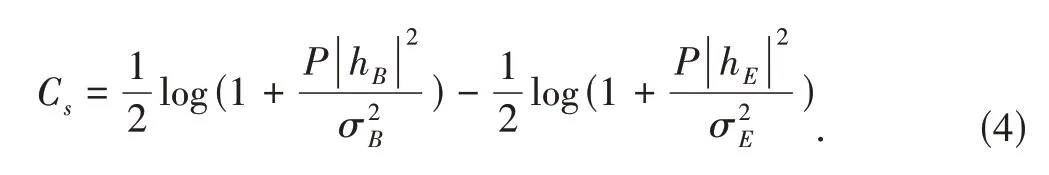
Note that the secrecy capacity in the Gaussian wiretap channel is equal to the difference between the legitimate channel’s Shannon capacityCMand the eavesdropper channel’s Shannon capacityCE,which can be formed as
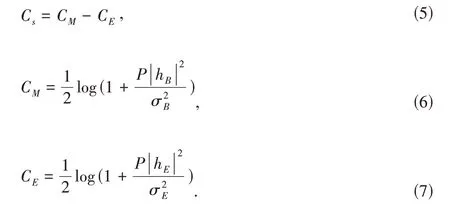
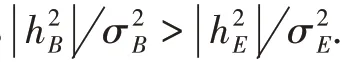
2.4 Secrecy Capacity
Another well-accepted PLS performance metric for the Gaussian wiretap channel is the secrecy outage probability introduced by BLOCH et al.[22]The secrecy outage is the event of instantaneous secrecy capacityCSlower than the target secrecy rateRS,which is {CS<RS}.The secrecy outage event will trigger the suspending of transmission.Thus,the outage probability is defined as

3 Physical Layer Security Techniques Under MmWave Channel
The mmWave is the spectrum from 30 GHz to 300 GHz.It is receiving lots of interest from academia,industry and government due to the limited available spectrum in sub-6 GHz bands and the advantage of gigabit-per-second data rates in mmWave[6,23–24].The hardware constraints,channel model and array size for mmWave are quite different from those for the spectrum below 6 GHz at which the carrier frequencies of most consumer wireless systems operate[4].First,more analogto-digital converters with higher resolution are required for mmWave,due to the higher frequency and bandwidth channel.Partitioning the operations into analog and digital domains for signal processing is a possible solution to these hardware constraints.In addition,the propagation environment has a different effect on the channel model because of the smaller wavelength of mmWave signals.Lastly,the array size for mmWave communications could be large,benefitting from the shorter wavelength of the mmWave.This section briefly surveys most recent research work in the PLS topics on DM,AN and DPC.
3.1 Directional Modulation
The DM is a technology that transmits digitally encoded signals to a specific direction while scrambling the other directions’ constellations of the same signal at the same time[25].In this way,confidential communications can be achieved between the transmitter and the designated receiver in the desired spatial direction.
The concept of DM was first introduced to phased arrays by DALY et al.[25]In DALY et al.’s scheme[25],the controlled radio frequency (RF) level analog PSs are added to each antenna of the phased array.By changing the phase weighting through the PSs at the symbol rate,a desired constellation is produced in the intended direction,while deliberately distorting the constellations in other directions.In addition,DALY et al.also implemented the proposed technique with a fourelement patch array in Ref.[26].In the implemented scheme,the genetic algorithm is employed to get the phase shift value of each antenna in order to achieve DM for the quadratic phase shift keying (QPSK) signal.However,DALY et al.’s scheme does not take the characteristics of different channels into account.The calculation of phase values with a genetic algorithm is time-consuming for a large-scale array.Many of the subsequent DM-based PLS schemes[27–31]are investigated for sub-6 GHz channels.
However,DALY et al.’s scheme[25]may be not suitable for the mmWave band system,which has the following characteristics.First,the small carrier wavelength of mmWave makes the implementation of large antenna arrays possible.The high pathloss of the mmWave band signal could be compensated with the high beamforming gain from the large array size[32].On the other hand,the larger array size increases the complexity of the design for PLS schemes.Second,the larger array size highlights the importance of system structure simplification due to the hardware cost constraint[4].Specifically,the RF chain cost is the dominant factor in the mmWave system with a large array size[33].Minimizing the number of RF chains can reduce the hardware cost and power consumption,which are key factors to support massive machine-type communication between resource constraints devices,especially IoT devices.Third,the scattering and multi-paths in the mmWave band are sparse.The propagation channel in the mmWave band,which is highly directional,has large path loss and very few multipaths[34].The majority of multipath components is determined by the line-of-sight (LOS) components[35].Thus,spatial sparsity commonly existing in mmWave channels poses new challenges and opportunities in designing efficient PLS schemes.
By taking advantage of the larger array size of the mmWave system,VALLIAPPAN et al.proposed a low-complexity DM scheme named Antenna Subset Modulation (ASM)[36].In VALLIAPPAN’s scheme,the array radiation pattern is modulated at the symbol rate to achieve DM.Only a subset of all the array antennas is used for transmission.The antenna subset used for transmission will change with the symbol rate.The subset for each symbol interval is selected from all subsets with the same number of the active antennas at random.As a result,randomness will be added to the constellations in all directions except the intended one.
VALLIAPPAN et al.’s ASM considers and takes the advantages of the large array size characteristic of mmWave system.The design of the constellation in ASM is much simpler.It only requires phase shifts or switching combinations to produce an expected modulation symbol for the user in the target direction.It is quite different from other previous DM techniques such as those in Refs.[26,37–38],which typically run optimization algorithms to obtain the correct set of weights.Because only the inter-antenna phase shift needs to be changed,it opens a new era for the DM application in PLS for the mmWave channel.However,ASM restricts the modulation type to phase modulation only.In addition,many of the antennas remain idle,especially when the RF chain size is much smaller than that of the antenna number.Furthermore,the switching speed must be the same as the data rates,which increases the hardware cost.
Based on VALLIAPPAN et al.’s scheme[38],ALOTAIBI et al.proposed a similar scheme named Switched Phase Array(SPA)[39].SPA modifies the ASM.In SPA,only one antenna is changed to be off to generate the constellation distortion in undesired directions.Thus,the system complexity is reduced while increasing the active antenna numbers used for transmission with higher gain in the main lobe.In addition,SPA can support both phase modulation and amplitude modulation and cause both phase and amplitude distortion in the undesired direction.
VALLIAPPAN et al.’s ASM[38]and ALOTAIBI et al.’s SPA[39]use the on-off switches to change the beamforming weight vector,which results in the scrambled constellation in the undesired direction.In their schemes,the beamforming weights are all binary.Neither ASM nor SPA takes full advantage of the full value range of beamforming weights to increase the difficulty for eavesdroppers to get the information.In addition,idle antennas exist in both ASM and SPA.The idle antennas neither contribute to the data transmission in the target direction nor generate the interference in the undesired direction.Motivated by the mentioned point,HONG et al.proposed a novel programmable weight phased array (PWPA)scheme[40].PWPA has a conventional phased-array architecture with a programmable power amplifier used to change the antenna weight element amplitude.Based on the idea of PWPA,HONG et al.[40]proposed an antenna subset transmission scheme with inverted antennas named Inverted Antenna Subset Transmission (IAST) first.In IAST,several antennas are selected to transmit with inverted signals,which is different from the on-off mechanism in ASM and SPA.IAST not only scrambles the constellation but also generates more AN than conventional schemes in the undesired directions.
In recent years,some new DM-based schemes were proposed to address challenges in new scenarios such as Cybertwin and reconfigurable intelligent surface (RIS).HE et al.[41]proposed a low-complexity phased-array PLS scheme for the mmWave communication in Cybertwin-driven V2X scenarios.Similar to the typical DM-based approach,a lightweight swapbased transmitting weight vector is utilized to periodically update the transmitting weight.An efficient algorithm based on the bisection method is also introduced to quickly obtain the initial weight vector at a low computational cost.YE et al.[42]considers that the additionally introduced beam to align to the RIS may cause high sidelobe,which has a significantly negative impact on the discrete optimization in antenna subset selection.To address such a challenge introduced by the RIS,a low sidelobe beamforming approach to enable DM-based PLS in RIS communication networks is proposed,by using a novel cross-entropy iterative method.
3.2 Artificial Noise
For PLS,the security capacity,one of the important performance metrics,is a function of the received signal SNR of legitimate receivers and eavesdroppers in the wireless Gaussian channel.For wireless channels,the received signal power will decrease with the increase of the distance between the transmitter and receiver.For this reason,it is possible that the eavesdropper may be placed in an undesired direction with a much closer distance to the transmitter.Even though the eavesdropper is in the lower order sidelobe of the transmitter beam,the received signal power of the eavesdropper may be still high enough to get an acceptable SNR due to the much smaller power fade of a shorter distance.As a result,the security capacity will be seriously deteriorated in this scenario.
To address this problem,a properly designed AN is added to the transmitted signal in order to degrade the SNR of the received signal by the eavesdropper.The concept of AN was first introduced by GOEL et al.[43]The application of AN in the PLS has been studied in a number of works since then.ASHISH et al.showed that the AN transmission can be secrecy capacity-achieving at high SNR for the multi-input,single-output,multi-eavesdropper (MISOME) wiretap channel,if the eavesdropper’s channel knowledge is known by the transmitter[44].This conclusion indicates that the AN is an effective technique for the PLS under certain conditions.ASHISH et al.’s work lays a solid theoretical foundation for AN-based physical layer security schemes.An optimal power allocation scheme that balanced the message and the AN transmission[45]was then studied for fading MIMO channels by ZHOU et al.Since then,a considerable number of studies have been conducted for AN-based PLS schemes.
However,most of the proposed schemes[43–49]focus on the sub-6 GHz channel.They neither take the hardware and cost constraints of the mmWave system into account,nor make use of the characteristics of the mmWave to additionally enhance the security.ZHAO et al.proposed a scheme named Phase-Only Zero Forcing (PZF) for secret communications[50],by using the AN technique for the mmWave channel.In the proposed scheme,ZHAO et al.fully considered the hardware cost constraints of the massive antenna system for mmWave.Specifically,each RF chain in the array is associated with an analog beamforming vector.All elements’ magnitudes must be constants,but they can have arbitrary phases.This constraint comes for two reasons.First,the full digital array with a digital beamforming vector requires each RF chain to be equipped with both the digital-to-analog converter (DAC) and analog-todigital converter (ADC).Due to the large array size of mmWave systems,which could be tens or even hundreds,the hardware cost of a full digital array system will be extremely high[51–52].Second,the constant magnitude weight has a lower peak-to-average power ratio (PAPR),which means the signal can be amplified with more affordable non-linear power amplifier (PA) with higher efficiency.Compared to expensive linear power PA,the non-linear power PA is more scalable for the mmWave system with a large array size[4,53].
ZHAO et al.’s main idea is to find a beamforming vector for AN transmitting in the null space of the legitimate receiver’s channel.Inspired by ZHAO et al.’s idea,XU et al.proposed a secure massive MIMO communication scheme[54]by taking advantage of the null-space of the user channel,which is constructed by the DACs with lower resolution.By projecting the AN into the null space of the legitimate receiver’s channel with proper power allocation between low-resolution or highresolution DACs,the PLS can be achieved.Specifically,XU et al.derived a closed-form SNR threshold to improve the secrecy rate.The threshold determines the choice between the DACs with low resolution or high resolution.A DAC quantization model is developed to support the analysis of the asymptotic achievable secrecy rate.In addition,XU et al.investigated secure communications over sparse mm-Wave massive MIMO channels.With consideration of the spatial sparsity of a legitimate user’s channel,XU et al.proposed a secure communication scheme in Ref.[55].Through a limited number of RF chains,the information data are precoded onto dominant angle components of the sparse channel.The AN is broadcast to the nondominant angles.Thus,only the eavesdroppers will be interfered with a high probability.With two defined statistical measures of the channel sparsity,XU et al.analytically characterized its impact on the secrecy rate.Analysis shows that a significant improvement in the secrecy rate is achieved,due to the uncertainty introduced by the unknown channel sparsity for the eavesdropper.
ELTAYEB et al.investigated the mmWave PLS in vehicular communication systems and proposed two AN-based schemes[56]for vehicular mmWave communication systems.By utilizing multiple antennas with a single RF chain,the first scheme implements the transmission of symbols to a target direction,while AN is sent in non-receiver directions.The second design uses multiple antennas with a few RF chains to transmit information symbols to a target user,while opportunistically injecting artificial noise in controlled directions.The purpose is to reduce interference in vehicular environments.
JU et al.comprehensively studied the secure transmissions in the mmWave decode-and-forward (DF) relay system[57].They investigated the optimal parameter design for the DF relay system under the same codeword transmission (SCT)scheme and the different codeword transmission (DCT)schemes.JU et al.derived the closed-form expressions for the secrecy outage probability and connection probability.Then a solution to the secrecy throughput maximization problem was given.Based on this work,JU et al.performed extensive experiments to investigate practical secure transmission problems for mmWave communication systems[58].They analyzed the vulnerability of existing defenses in practice and found that the existing defenses in Refs.[36] and [56] had vulnerabilities,because they might have impractical hardware requirements or still be vulnerable against multiple colluding eavesdroppers.Finally,JU et al.proposed the artificial noise hopping (ANH) with minimal hardware complexity to effectively enhance the security.
LIN et al.investigated the scenario of a 5G cellular network coexisting with a satellite network in Ref.[59].By employing a ULA at the base station (BS) and assuming the imperfect angle-of-arrival-based channel state information (CSI) of multiple eavesdroppers (Eves) is known,a constrained optimization problem is formulated.Under the constraints that are the transmit power of BS and the interference threshold of the satellite earth station,the achievable secrecy rate of the cellular user under the worst case can be maximized.
LIN et al.proposed two robust beamforming methods to solve the complex optimization problem,in the case of either coordinated or uncoordinated Eves.They also investigated the secure communication of a cognitive satellite terrestrial network with the software-defined architecture in Ref.[60].In LIN’s scheme,the interference from the terrestrial network can be regarded as a green source to enhance the physicallayer security for the satellite network.With this assumption,a constrained joint optimization problem is formulated to minimize the total transmit power.The optimization satisfies both the terrestrial users’ quality-of-service requirement and the satellite users’ secrecy rate requirements.
Different from many schemes focusing on protecting the downlink transmission,XU et al.[61]proposed a scheme to protect the uplink transmission for the massive MIMO system with AN-based approaches.By optimizing the power allocation between AN and data symbols,the maximum secrecy rate can be formulated.
3.3 Directional Precoding
The DPC is commonly used in the MIMO system to improve system performance by forming the beam in certain directions,which can concentrate the power in those directions.It can be also used in the PLS to protect the secrecy of the legitimate receiver,by adding additional constraints for the power leaking to the undesired directions.A lot of PLS schemes based on DPC[62–67]have been proposed.However,most of them are designed for the sub-6 GHz environment.There is no special consideration for the characteristics of the mmWave environment,especially the large array size and hardware constraints.
To support the PLS under both multiple legitimate receivers and multiple eavesdroppers,HUANG et al.proposed a constant envelope (CE) hybrid precoding scheme (CEP)[68].A unified CE hybrid precoding framework is introduced for the sub-connected digital and analog hybrid mmWave system to protect communication secrecy.By solving an optimization problem,the qualities of target users’ received constellations are guaranteed.It minimizes the power leaked to the possible eavesdroppers.To address the high hardware cost issue with the large array size mmWave system,HUANG et al.applied two measures in the proposed scheme.First,a digital and analog hybrid MIMO architecture with a much reduced number of RF chains is adopted to reduce the high hardware cost and energy consumption of mmWave RF chains.Second,only the CE signal with low PAPR,which can be amplified with high power efficiency but low-cost non-linear PA,is transmitted through the array.
CHEN et al.investigated a novel hybrid beamforming design[62]to jointly optimize the data precoding and the AN power fraction selection in the massive MIMO system.To solve the non-convex secrecy rate maximization problem for hybrid precoder design,CHEN et al.separated the design for analog and digital precoders.The analog precoder was used to maximize corresponding channel gain in the analog data precoder design.In the digital data precoder design,an iterative algorithm was proposed for the optimal design with the removed non-convex codebook constraint.
LI et al.systematically investigated the impact of lowresolution PS on hybrid beamforming under various scenarios[63–71].Specifically,for a wideband mmWave multipleinput and multiple-output orthogonal frequency-division multiplexing (MIMO-OFDM) system,LI et al.introduced a novel hybrid beamforming architecture[63]with varying antenna subarrays and efficient low-resolution PSs.The performance loss due to the employment of practical low-resolution PSs can be mitigated with the multiple-antenna diversity,which comes from the dynamic connection for each RF chain to a nonoverlapping antenna subarray with the help of a switch network and PSs.For the architecture of dynamic hybrid beamforming,they jointly designed the hybrid precoder and combiner to maximize the average spectral efficiency.However,they did not consider the impact of low-resolution PSs on PLS.
3.4 Other PLS Schemes
The principle of AN techniques is to send jamming signals to degrade the eavesdropper channel capacity in order to improve the secrecy capacity of the legitimate channel.The jamming signal may be sent from the main transmitter or other friendly users.In this way,the main transmitter can work with other friendly receivers to cooperatively degrade the eavesdropper channel capacity.This technique is called cooperative jamming (CJ),which was first introduced by DONG et al.[72]
HU et al.investigated cooperative secret communications in wireless networks with multiple passive eavesdroppers,without the knowledge of legitimate users’ perfect CSI but only eavesdroppers’ statistical CSI.The secrecy beamforming with AN and CJ are explored to enhance secrecy[73].The closed-form secrecy outage probability expression is derived.HU et al.concluded the condition that a positive secrecy rate could be achievable.Finally,a secure transmission with AN and CJ design,which maximizes the secrecy outage probability with a constrained secrecy rate,is proposed.
Motivated by HU’s work,SONG et al.proposed an enhanced scheme with weaker CSI assumptions[74].In SONG et al.’s scheme,only the knowledge of the statistic CSI of illegitimate channels and the imperfect CSI of legitimate channels are known.They derived the optimal power allocation ratio between the information-bearing signal and the AN signal in order to maximize the secrecy rate.Under the statistic CSI of illegitimate channels and the imperfect CSI of legitimate channels,the optimal power allocation,which balances the information bearing signal and the AN signal,is derived to achieve the max secrecy rate.
The mmWave PLS in UAV is another hot topic with significant attention in recent years.LI et al.investigated a secure communication system[75],which considers the smart attack from another UAV besides the legitimate UAVs.LI et al.also considered the practical cases in communications.The first is that the limited number of pilot signals may exist for channel estimation.The second is that the receiver side’s channel estimation may be imperfect.To address the problems brought by the imperfect channel estimation and smart attackers who choose different kinds of attacks on the basis of the continuously changing channel environments,LI et al.used the noncooperative game theory to derive a Q-learning-based power control algorithm,which obtains an adaptive policy for the transmitter.MA et al.investigated the secure mmWave communications assisted by multiple UAV-enabled relays,together with eavesdroppers[76],under the model of randomly distributed eavesdroppers on the ground.With the models of 3Dantenna gain and stochastic geometry,the characteristics of air-to-ground channels are considered for deriving the closed form expressions of secrecy outage probability based opportunistic relay selection.It is demonstrated that the secrecy improves when the relay density increases.For mmWave MIMOOFDM systems with dynamic subarray (DS),SUN et al.proposed a machine learning based hybrid precoding scheme[77].The scheme presents a shared agglomerative hierarchical clustering (shared-AHC) algorithm for DS grouping to improve spectral efficiency (SE) performance.
3.5 Comparison
The techniques for mmWave PLS can be classified into three categories based on their technical patterns: DM,AN and DPC.Their characteristics are summarized in Table 2.

▼Table 2.Cost and power efficiency comparison of mmWave physical layer security (PLS) techniques
Specifically,the DM technique depends on the weight vector codebook.It achieves PLS by randomly selecting the vector from the codebook.The computation cost to get the codebook may be either low or high depending on the scheme and codebook size.If the scheme randomly selects the antenna subset just as what the scheme ASM does,there is only a very tiny computation cost.On the other hand,if the sechem,like Polygon,constructs the codebook with an infinite size,the computation cost may be high.The other two techniques are different from the DM technique,which are usually based on optimized weight vector results under certain security constraints.The optimization calculation may be quite complex.However,once getting the results,the weight vector will normally not change at the symbol rate.Thus,high-speed switch is not required as that in DM-based schemes.
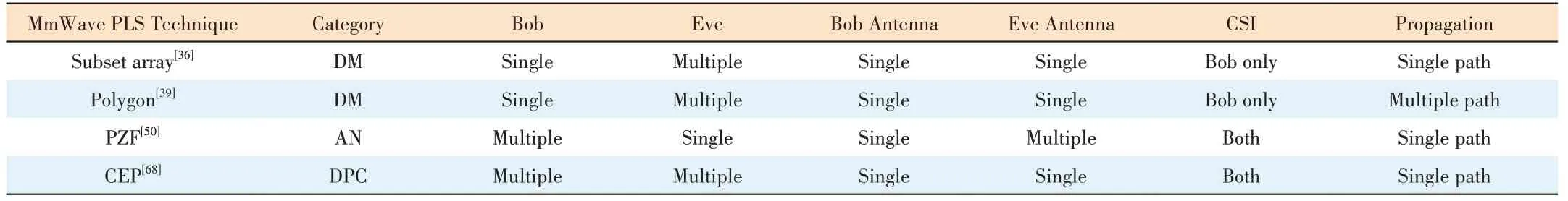
A detailed comparison of the typical mmWave PLS schemes is shown in Table 3.Different schemes with different advantages and shortcomings are suitable for different scenarios.The subset array scheme[36]utilizes the characteristic of the large array size of the mmWave system to enable PLS.However,it is only suitable for single path scenarios.The polygon scheme[39]can work under a multiple-path scenario with a different approach.It should be noticed that current DMbased mmWave PLS schemes only support single-target receiver scenarios.It significantly constrains its application in massive machine-type communication scenarios,where multiple target receivers usually exist.To support multiple Bobs,the AN approach is usually adopted,but it comes with the cost of low power efficiency,which may be not friendly to mobile devices.In addition,the AN-based scheme proposed in Ref.[50] requires the CSI on both Bob and Eve.It may be not practical to meet such the condition,since Eve may not be exposed.The DPC-based scheme in Ref.[68] can work for multiple Bobs and multiple Eves at a high cost on both hardware and computational resource.
4 Future Research Problems
In this section,we discuss three future research problems for the PLS-based mmWave environment.
4.1 Low Complexity Directional Modulation Weight Vector Codebook Construction
The DM-based PLS schemes rely on randomly selecting the weight vector from the codebook.The codebook must be constructed before the actual transmission.However,the codebook is highly related to the target receiver’s relative direction to the transmitter.Once the relative direction between the transmitter and the target receiver changes,the whole codebook has to be reconstructed.For current DMbased PLS schemes[36,39,40,46],although the hardware cost has been minimized by adopting various techniques such as constant envelope,on-off switch and subarray,the algorithms for codebook construction all still suffer high complexity and high time consumption.This fact makes these schemes hardly adapt to highly dynamic scenarios with frequent and quick relative direction changes,such as vehicle networks and UAV networks,which require the codebook to be reconstructed within a short time.Since mobility is an important feature of the massive machine-type communication scenario,the DM PLS scheme with low complexity codebook construction algorithm is preferred.Motivated by this demand,the research will be conducted on reducing the DM codebook construction algorithm complexity.One of the challenges is how to maintain the PLS while reducing the codebook construction computation cost.Another challenge is how to balance the hardware cost and the codebook construction algorithm complexity.
▼Table 3.Property comparison of mmWave physical layer security (PLS) schemes
4.2 Impact of Phase Shifter with Finite Precision on PLS
For the DM-based mmWave PLS schemes,the PS is a critical component to change the weight vector in order to achieve PLS.However,similar to all other hardware,the PS cannot ideally operate as it is expected in the theory.The actual shift phase value may be different from the expected value due to the limited precision of the hardware.It causes a truncation error in the PS.The effect of the truncation error of the PS can hardly be ignored.A dynamic antenna subarray approach in Ref.[63] is introduced to mitigate the performance loss due to the employment of practical lowresolution PSs.However,this approach only focuses on the communication performance enhancement of the target receiver.Its motivation does not come from the view of PLS.The impact of low-resolution PSs on the PLS performance has not been fully investigated.Thus,many opening questions need to be addressed and researched for the impact of finite precision PS on the PLS.How to describe and measure the truncation error in DM-based PLS schemes? Is there any possibility to take advantage of the truncation error to construct new DM-based PLS schemes? These questions pose both opportunities and challenges to the DM-based mmWave PLS schemes.
4.3 Multiple Target Receivers Supported Direction Modulation
Most of the DM-based PLS schemes for mmWave can only support one target receiver,by placing the target receiver in the main lobe.It limits the application to massive machine-type communication scenarios such as IoT device networks,which often require multicast communications to multiple target receivers.The scheme in Ref.[31] provides a multiple target receiver supported DM approach by utilizing the retrodirective array antenna.However,the retrodirective array antenna suffers serious performance degrading under the mmWave band[78].The hardware cost will also increase dramatically by implementing the retrodirective array antenna with a large array size.The IoT device network with a large number of devices can hardly afford such a high cost.Thus,this approach is not suitable for the massive machine-type communication under mmWave.The approaches in Refs.[79–81] provide multi-beam DM solutions to supporting multiple target receivers.However,they do not consider the fact that multiple target receivers may locate in the same direction with different ranges to the transmitter in practical scenarios.Thus,the multi-beam solution cannot fully adapt to the multiple target receiver scenarios.Motivated by the demand on multiple target user support in the massive machine-type communication,the research for multiple target user supported DM will be conducted.The major challenge is how to distinguish different target receivers in both the angular domain and range domain,while protecting their PLS.
5 Conclusions
In this paper,we introduce the concept of PLS together with its importance to the mmWave 5G network,and discuss the typical PLS techniques including DM,AN and DPC.By literature reviewing the PLS schemes based on each PLS technique in detail,we summary the advantages and constraints of the DM,AN and directional precoding technique for the mmWave PLS.Finally,we propose several future research problems on mmWave PLS.Specifically,the multiple target receivers supported DM and the impact of PS with finite precision on PLS have not been fully investigated for the mmWave PLS.The computation cost for DM weight vector codebook construction is still too high to make the DM-based PLS solution adapt to highly dynamic massive machine-type communication scenarios.It is expected to draw more attention and efforts to addressing these interesting open problems in PLS-based mmWave communications.
- ZTE Communications的其它文章
- ZTE Communications Guidelines for Authors
- Table of Contents,Volume 20,2022
- Broadband Sequential Load-Modulated Balanced Amplifier Using Coupler-PA Co-Design Approach
- A Unified Deep Learning Method for CSI Feedback in Massive MIMO Systems
- A Content-Aware Bitrate Selection Method Using Multi-Step Prediction for 360-Degree Video Streaming
- Label Enhancement for Scene Text Detection

