Cluster Head Selection Algorithm for UAV Assisted Clustered IoT Network Utilizing Blockchain
(Huazhong University of Science and Technology,Wuhan 430074,China)
Abstract:To guarantee the security of Internet of Things (IoT)devices,the blockchain tech?nology is often applied to clustered IoT networks.However,cluster heads (CHs) need to un?dertake additional control tasks.For battery-powered IoT devices,the conventional CH se?lection algorithm is limited.Based on the above problem,an unmanned aerial vehicle(UAV)network assisted clustered IoT system is proposed,and a corresponding UAV CH se?lection algorithm is designed.In this scheme,UAVs are selected as CHs to serve IoT clus?ters.The proposed CH selection algorithm considers the maximal transmit power,residual energy and distance information of UAVs,which can greatly extend the working life of IoT clusters.Through Monte Carlo simulation,the key performance indexes of the system,in?cluding energy consumption,average secrecy rate and the maximal number of data packets received by the base station (BS),are evaluated.The simulation results show that the pro?posed algorithm has great advantages compared with the existing CH selection algorithms.
Keywords:cluster head selection;unmanned aerial vehicle;blockchain;IoT;average secrecy rate
1 Introduction
With the development of fifth-generation (5G) net?works,which provide extended coverage,higher throughput,lower latency and higher connection density with a massive bandwidth,5G based Inter?net of Things (5G-IoT) devices have emerged as small-size,low-cost,typically battery-powered and densely distributed de?vices to support large-scale information exchange.Therefore,the 5G-IoT is a core component of the future network.On the one hand,the evolution of 5G networking not only has paved the way for the connection of massive IoT nodes to the Internet to facilitate the advancement of various IoT applications from theory to reality,but also has led to the proposal of various po?tential technologies,such as millimeter-wave,massive multi?ple-input multiple-output and device-to-device.On the other hand,over 75 billion devices will be connected to the IoT by 2025,which is expected to have a dramatic impact on our lives in the near future[1].This will be beneficial for support?ing networks in generating enormous amounts of information traffic,enabling humans to obtain messages about anything and anyone at any time and any place (4A)[2].Despite the fruitful developments in 5G-IoT communications,several is?sues that hamper effective IoT communication in 5G networks remain unsolved,including redundancy in data,dynamic size of the network,less reliable medium,heterogeneous network,and multiple base stations (BSs)or sink nodes.To process da?ta in a distributed way,remove redundant data and improve the energy efficiency,the IoT system needs to adopt clustering technology[3].Clustering builds a hierarchy of clusters or groups of sensing nodes that collects and transfers the data to its respective cluster heads (CHs).The CH then groups and sends the data to the sink node or BS.The CHs act as middle?ware between the end user and the network,so the selection of CHs is particularly important[4].
Due to the limited computing capacity and energy of IoT de?vices in the process of data transmission,it is difficult to adopt highly complex algorithms and frameworks to ensure the data security.Therefore,IoT devices face many security issues that include the authenticity and confidentiality of data[1].Block?chain,which can guarantee the integrity,transparency and se?curity of data in industrial data processing,has attracted great attention in the application of IoT[5].Integrating blockchain and IoT has many advantages.Firstly,it can improve resil?ience and adaptability of the IoT system.Blockchain can store redundant replicas of data in the form of transactions over blockchain nodes,which helps to maintain data integrity and provide resilience to the IoT system.Secondly,since block?chain is a distributed ledger,using blockchain as the data management mechanism for the IoT can adapt to varying envi?ronments and use cases to meet the growing needs and de?mands of IoT devices,which improves the adaptability of the system.Finally,integrating blockchain and IoT can enhance the fault tolerance and security of the whole system.However,due to the verification of blockchain,IoT devices will perform additional computing tasks,which will greatly increase energy consumption and reduce the service life of IoT systems.
Considering the energy limitation of IoT devices,there are many clustering technologies and CH selection algorithms to reduce energy consumption of the IoT system.HEINZELMAN et al.proposed a low-energy adaptive clustering hierarchy(LEACH) protocol[6],in which CHs were randomly selected in each round.Since the selection of CHs is random,the nodes with low energy are at the same priority as those with high en?ergy.If the nodes with low energy are selected as CHs,they will fail quickly,thus shortening the network life.Based on the LEACH,TRUPTI et al.proposed a CH selection algorithm based on residual energy,which is to choose the devices with more residual energy as the CH[4].YOUNIS et al.adopted the hybrid energy efficient distributed clustering (HEED) algo?rithm,which could select devices with high battery power as the CH through the proposed iterative CH selection algo?rithm[7].In the above works,wireless sensors or IoT devices are selected as CHs.Although the energy limits of devices are considered in these algorithms when selecting CHs,the ener?gy limitations of IoT devices will lead to frequent failure,re?sulting in more system energy consumption.AADIL et al.pro?posed energy aware link-based clustering (EALC),which adds two other parameters (energy level and distance) to the neigh?borhood to select the optimal CH.EALC extends cluster life and reduces energy consumption[8].
Due to the large difference of devices and limited resources of the blockchain-based IoT system,which needs to perform additional blockchain computing tasks,the choice of IoT de?vices as the CHs will have great limitations.The emergence of unmanned aerial vehicles (UAVs) provides new opportunities for the blockchain-based IoT system.When UAVs are used as flying BSs,they can support the connectivity of existing ground wireless networks to help land systems achieve good coverage and effectively reduce the data traffic of other BSs.Moreover,as devices with flexible deployment,UAVs are equipped with high-performance calculators with high comput?ing capacity,which can quickly respond to the communication and computing needs of IoT devices,thus improving the quali?ty of service[9].In addition,solar-powered UAVs can convert solar energy into electric energy,thus increasing its service time[10].Moreover,a large number of UAVs can cooperate with each other through relay nodes to build a self-organizing intel?ligent UAVs network to complete complex tasks[11].Therefore,it has great advantages to choose UAVs as CHs.
To solve the problems of limited resources and security faced by IoT clusters,the main contributions of this paper are as follows.Firstly,the UAV network served IoT cluster system is built.To ensure the security of data,the IoT devices in the system use blockchain technology to store data.Secondly,we propose a UAV CH selection algorithm.The algorithm jointly considers the distance between UAVs and IoT devices,the distance between UAVs and BSs,residual energy,and the maximal transmit power of UAVs.The IoT devices calculate the corresponding weighted value of the UAV through the pro?posed algorithm,and choose the UAV with the smallest weighted value to vote.The UAV with the most votes serves the IoT cluster as the CH.Finally,based on the proposed algo?rithm,this paper evaluates several performance indicators such as the energy consumption of the IoT cluster,the average secrecy rate and the maximal number of packets received by the BS,and compares the performance with several existing CH selection algorithms,which demonstrates the superiority of the proposed algorithm.
This paper is structured as follows.Section 2 presents our system model and the basic procedure of the practical Byzan?tine fault tolerance (PBFT) consensus algorithm.Moreover,we use received signal strength (RSS) technology to estimate the distance between IoT devices and UAVs in this section.In Section 3,we propose a UAV selection algorithm based on a private blockchain and introduce performance evaluation indi?cators.The simulation results are analyzed in Section 4.Final?ly,Section 5 concludes this paper.
2 System Model
2.1 Network Topology
To enable secure energy-efficient communication,a block?chain-based CH selection algorithm is proposed in this paper.As shown in Fig.1,a blockchain-based clustered IoT net?work,where a UAV swarm composed ofMUAVs,denoted by set{U1,U2,U3,...,UM},is deployed to serveSIoT clusters,de?noted by set {C1,C2,C3,...,CS}.Each IoT cluster containsKIoT devices,denoted by set {D1,D2,D3,...,DK}.To reduce the power consumption of the IoT devices during data transmis?sion,UAVs hovering in the sky collect data from the IoT de?vices before transmitting the collected data to the BS.Mean?while,the IoT clusters adopt private blockchain technology to protect their collected data and to facilitate secure communi?cation.Eavesdroppers coexisting with the IoT clusters may in?tercept the transmitted data.We assume that the IoT devices and the UAVs can establish Line-of-Sight (LoS) communica?tion links for data transmission.In contrast,an eavesdropper may experience a Rayleigh fading channel while eavesdrop on the IoT devices.The UAVs first broadcast a message contain?ing the pilot signal and the UAV information to the IoT devic?es.The IoT devices in each cluster use blockchain technology to verify the information received from UAVs and estimate the distance to each UAV.Using the proposed CH selection algo?rithm,the IoT devices in each cluster then vote through the PBFT consensus algorithm.According to the voting results,the UAV that receives the most votes from the cluster is select?ed as the CH.When different clusters choose the same UAV as the CH,it is assumed that when the energy of the UAV se?lected by a cluster is exhausted,that cluster will select a dif?ferent UAV.The IoT devices in each cluster communicate us?ing orthogonal frequency division multiple access (OFDMA)technology,with a system bandwidth ofBHz.
2.2 Message Broadcasted by UAVs
As the first step of the blockchain-based CH selection pro?cess,theMUAVs first broadcast messageImto all IoT devices in the area.The message content includes the serial number of the UAVs,Um,which ranges from 1 toMfor the considered UAV swarm;the maximal transmit power of the UAV,Pm;the remaining energy in the battery of the UAVEm;the distance between UAVmand BSwhich is estimated at the BS by measuring the pilot signal of the UAV.The IoT devices can obtain the message of the UAV from the mark bit named Mark Signa.
2.3 Distance Estimation Based on RSS
In practice,the channel state information (CSI)between IoT devices and UAVs is unknown.To evaluate the CSI,the IoT devices usually adopt distance estimation.On the one hand,a UAV flying in the sky can provide a LoS propagation environ?ment,which is beneficial for evaluating the distances between the IoT devices and the UAV.On the other hand,the IoT de?vices are powered by batteries and have a simple hardware structure,and it is difficult for them to perform complex signal processing to obtain the CSI.Therefore,distance estimation based on RSS of an IoT device is suitable for UAV-assisted IoT communication[12].
In particular,after the messages broadcast by the UAVs are received by the IoT devices,each IoT device will estimate the distance to each UAV based on the RSS.By utilizing the RSS at the IoT device and the information of the UAV’s maximal transmit power provided in the broadcast message,the dis?tance between an IoT device and a UAV can be formulated through maximum likelihood estimation as follows:

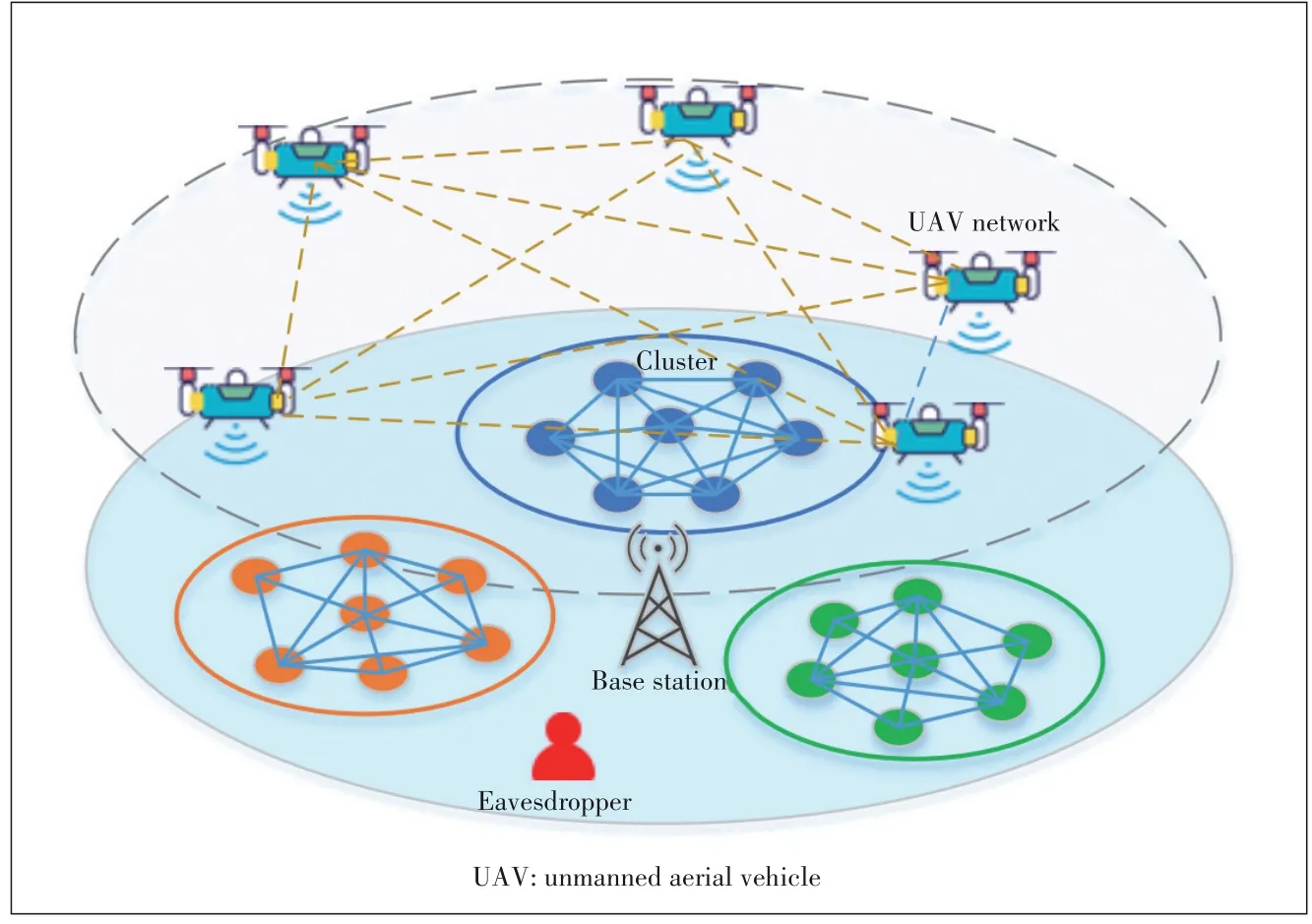
▲Figure 1.UAV assisted clustered IoT network utilizing blockchain
wherePmkis the signal strength received by IoT devicekfrom UAVm,i.e.,the RSS;Pmis the maximal transmit power of UAVm,which is specified in the broadcast message;npis the path loss factor.
2.4 Private Blockchain Constructed for IoT Clusters
To ensure data security,the IoT devices adopt a private blockchain to verify their col?lected data.Specifically,the IoT devices trans?mit their received messages broadcast from the UAVs to other IoT devices in the same cluster as transactions and then apply the PBFT algorithm to reach agreement.The con?sensus data will be stored in blocks in the form of transaction,and each block contains the hash code of the previous block,thus form?ing a blockchain.To ensure the privacy and security of the data in the PBFT process,a hash algorithm and an asymmetric encryption algorithm are introduced.We use the elliptic curve encryption(ECC) algorithm and Secure Hash Algorithm-256 (SHA-256)to detect whether transactions have been tampered with dur?ing data transmission[13].The encryption process is shown in Fig.2.By using SHA-256,we can generate a Merkle root,which can be used to effectively compress the amount of data to link each block.When using encrypted data,the IoT devic?es can perform the same hash calculation and compare the hash codes to verify the data.The ECC algorithm is used to generate public and private keys to encrypt the data.The data in the database will be encrypted into ciphertext by using the public key.Each user should provide his or her own private key to decrypt the encrypted message used for the custom ser?vice.These two algorithms can ensure the privacy of the data and prevent illegal operations.The consensus process of PBFT is shown in Fig.2 which contains the following phases:?Request phase:We refer to the IoT device that needs to pub?lish transactions as a client.In our model,IoT devices not on?ly act as the publisher of transactions,but also as the verifier of transactions.Before IoT devices transmit data to other nodes for verification,they need to encrypt the data.
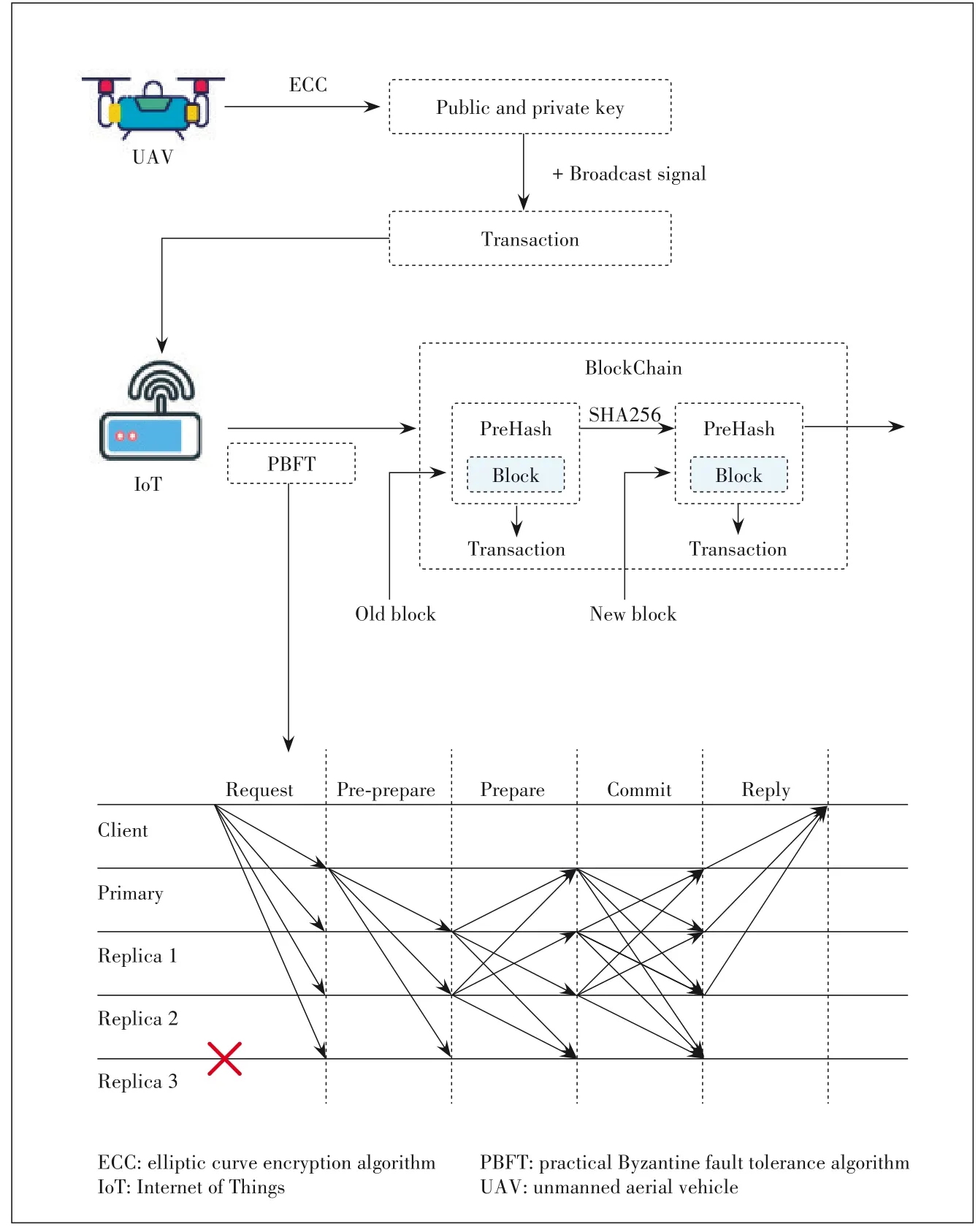
▲Figure 2.Private blockchain constructed for IoT clusters and PBFT process
? Pre-prepare phase:After receiving the message from the cli?ent,the primary node will assign an integer sequence number to the request,and then generate the pre-prepare message.The primary node then broadcasts the pre-prepared message to replica nodes.
? Prepare phase:The replica nodes verify the message that has not been tampered with,and then send a prepare message to other nodes.
? Commit phase:After verifying that all the prepared messag?es have not been tampered with,all nodes will broadcast the confirm message to other nodes.
? Reply phase:After verifying the message,all nodes will re?turn the result to the client.
2.5 System Performance Metrics
To analyze the performance of the CH selec?tion algorithm proposed in this paper,several important system parameters will be used.The CH selection process consists of four steps:An IoT cluster receives the broadcast messag?es from the UAVs,each IoT device chooses a UAV to serve as the CH based on the received messages,the IoT devices in the IoT cluster achieve consensus through the PBFT algo?rithm,and the IoT cluster sends a response message to the UAV swarm indicating the cho?sen CH.We utilize the energy consumption for CH selection to represent the system re?source consumption of the IoT cluster.Mean?while,system performance metrics,i.e.,the average secret rate and the maximal number of received packets,will be used to evaluate the gain of our proposed algorithm.
? CH selection energy consumption:CH se?lection delay refers to the time taken by a clus?ter from receiving UAV signal to reaching con?sensus and finally sending the selection result to the selected UAV,which reflects the effec?tiveness of CH selection algorithm.Large time delay will lead to large energy consumption,which will affect the life cycle of the device.
? Average secrecy rate:The secrecy rate is a key design metric for IoT networks that is wide?ly adopted for evaluating physical layer securi?ty is the secrecy rate.High secrecy rate will re?duce the probability of data eavesdropping.
? Maximal number of packets received by the BS:The number of packets received by the BS reflects the throughput of the system,which is a very important measure of the system.
3 Working Model
3.1 UAV Selection Algorithm
Based on the messages broadcast by the UAVs,all IoT de?vices in a cluster adopt the PBFT algorithm to verify their re?ceived messages to achieve consensus.Then,the IoT cluster chooses a UAV from the UAV swarm as its CH by following steps.
? Step 1:According to Eq.(3),each of theKIoT devices in the IoT cluster estimates the distancedmkfrom each UAV based on the RSS.
? Step 2:The distance between the BS and them-th UAV,denoted bycan be determined from the broadcast informa?tion sent by the UAV.
? Step 3:From the broadcast messages sent by the UAVs,the IoT devices are informed of the remaining energy of each UAV,Em.For each UAV,the energy ratio of the total remain?ing energy of all UAVs to the remaining energy of that UAV is

? Step 4:From the messages broadcast by the UAVs,the IoT devices are also informed of the maximal transmit power of each UAV,Pm.For each UAV,the ratio of the total maximal output power of all UAVs to the transmit output power of that UAV is

? Step 5:The weighted value of each UAV is computed as follows:
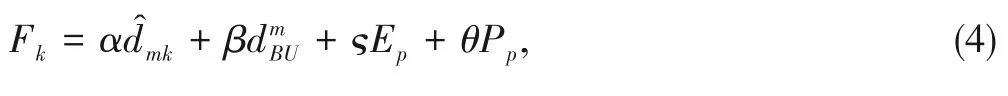
whereα,β,?andθare weighting factors that satisfyα+β+?+θ=1.
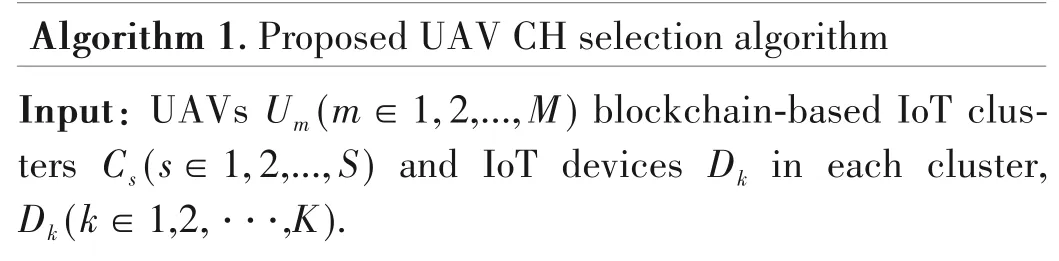
? Step 6:Each IoT device calculates its corresponding weighted valueFkfor each UAV following the above method.Then,thek-th IoT device votes for the UAV with the smallestFkto serve as the CH.All IoT devices in the same IoT cluster use the PBFT algorithm to vote for consensus.Finally,the UAV with the most votes is chosen to serve the entire cluster.The proposed CH selection process is presented in Algo?rithm 1.

3.2 Performance Metrics
3.2.1 Energy Consumption for CH Selection
In our system,the energy consumption of an IoT device mainly includes three components:the energy consumption for data transmission,the energy consumption for data re?ception,and the energy consumption for computing us?ing the PBFT algorithm,.For a UAV swarm composed ofMUAVs and an IoT cluster withKIoT devices,each IoT de?vice in the cluster will transmit 3Ktransactions,receive(M+2K-1) transactions,and perform(2K-1) computing opera?tions during the PBFT process.
The energy consumption of each IoT device during the pro?cess of transmitting transactions is calculated as[14]
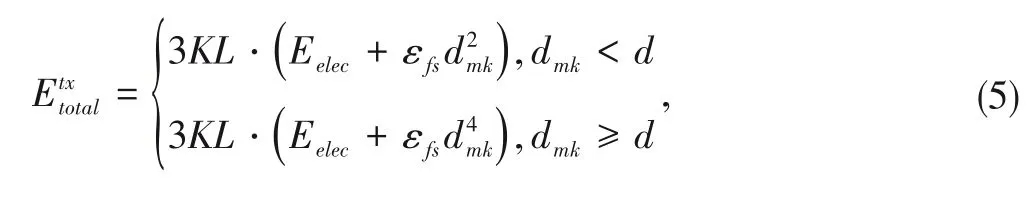
whereEelecis the energy dissipated per bit to run the transmit?ter or receiver circuit,andare the energy cost of a single amplifier under the two communication models depend?ing on the distance between the transmitter and receiver,anddis the threshold value.
The energy consumption of each IoT device during the pro?cess of receiving transactions is calculated as
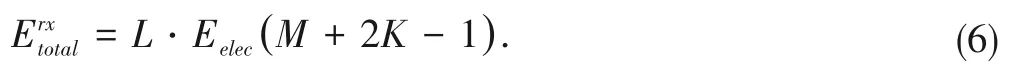
The energy consumption of each IoT device during the pro?cess of verifying transactions is calculated as

wheresmis the number of rotations required to calculate 1 bit of data,kmis the calculation efficiency andfkis the computing capacity of thek-th IoT device.
Considering that there areKIoT devices in the IoT cluster,the total energy consumed by all devices in the cluster for PBFT processing is calculated as
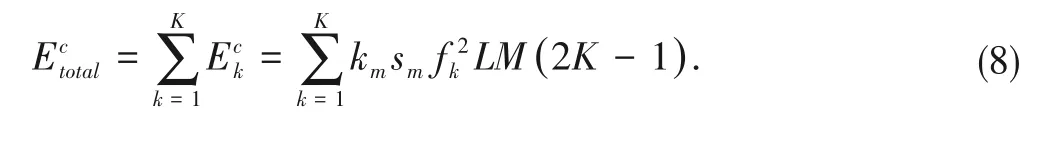
In the end,the total energy consumption of the IoT cluster for selecting them-th UAV in the UAV swarm as the CH is

For allSIoT clusters,the total energy consumption is ob?tained as follows:

3.2.2 Average Secrecy Rate of IoT Clusters
A diagram of the system secrecy rate is shown in Fig.3.When the strength of legitimate links is greater than that of eavesdropping links,a nonzero secrecy rate will be achieved[15].When them-th UAV in the UAV swarm is chosen as the CH for an IoT cluster,the information transmitted from the IoT devices to the UAV CH and from the UAV CH to the BS can be eavesdropped on.Therefore,the secrecy rates of both types of links are analyzed in the following.
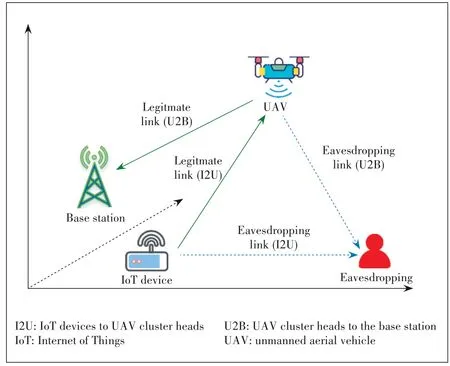
▲Figure 3.Diagram of system secrecy rate
For the information transmission from IoT devicekto the UAV CH,i.e.,UAVm,the achievable rate is obtained as fol?lows:

wherePkis the transmission power of IoT devicek,β0is the signal gain at a distanced0=1 m,σ2is the noise power anddmkis the distance between IoT devicekand the chosen UAVm.
For the information transmission from UAV CH to the BS,the achievable rate is obtained as follows:
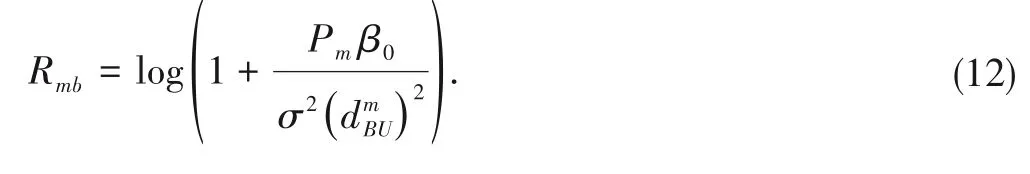
When there is an eavesdropper,the transmission rate from an IoT device to the eavesdropper is calculated as

wheredkeis the distance between IoT devicekand the eaves?dropper,andγis the path loss exponent.
For the eavesdropping link from a UAV to the eavesdrop?per,the transmission rate is calculated as

wheredmeis the distance between UAVmand the eavesdropper.
The average secrecy rate of an IoT cluster is
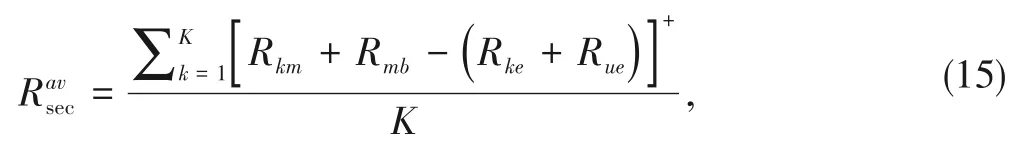
where[x]+=max(x,0).
For all theSIoT clusters,the total average secrecy rate can be calculated as follows:

3.2.3 Maximal Number of Packets received by BS
The number of packets received by the BS is an important indicator of the total throughput for an IoT cluster.When an IoT device transmits data packets comprisingLkbits to its UAV CH in each time slot and the UAV CH retransmits these data packets to the BS,the time consumed for the IoT device to transmit data to the UAV CH is

The IoT devices within an IoT cluster utilize the OFDMA scheme to transmit their data packets to the UAV CH,and hence,the total time consumed by the IoT cluster to transmit data to the UAV CH is

When the UAV CH retransmits these data packets to the BS,the UAV CH can utilize the whole usable bandwidth,and hence,the consumed time is
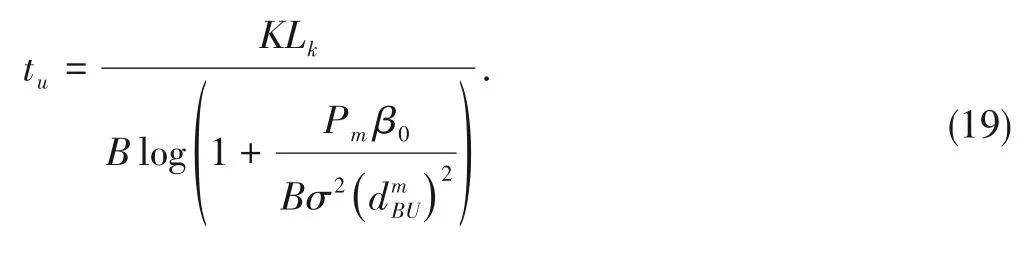
Meanwhile,the UAV also consumes propulsion power to support it as it flies in the sky.It should be noted that if the UAV uses up its energy between communication and propul?sion,the UAV will be unable to retransmit the data packets,and the CH will break down.According to Ref.[16],the power consumed for propulsion is calculated as

whereδdis the profile drag coefficient,ρis the air density,sis the robustness of the rotor,Ais the area of the rotor,andRis the radius of the rotor.
Each time a data packet is sent,the energy consumption of the UAV is
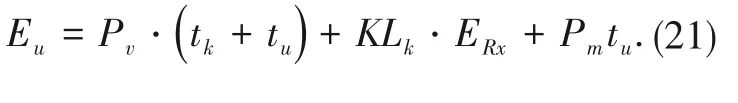
The maximal number of packets that UAVmcan transmit is

Thus,the maximal number of packets re?ceived by the BS is

4 Performance Analysis and Simulation Results
In this section,numerical results are pre?sented for evaluating the performance of the proposed CH se?lection algorithm.We compare our proposed CH selection scheme with other existing CH selection schemes,such as Low-Energy Adaptive Clustering Hierarchy (LEACH)[6],Hy?brid Energy-Efficient Distributed Clustering (HEED)[7]and Energy Aware Link-Based Clustering (EALC)[8].To illustrate the advantages of our proposed algorithm for blockchainbased IoT clusters,we use the existing CH selection algo?rithms as baselines for selecting UAV CHs and compare the system performance in each case with that achieved using the algorithm proposed in this paper.The simulation parameters are shown in Table 1.
4.1 Analysis of Security
1) Data trustworthiness:Data trustworthiness greatly af?fects the security of the collected data.Malicious nodes may insert fake data into the network and interfere with normal nodes,which may cause node failure.Our system uses the PBFT consensus algorithm,which has an error tolerance rate of(N-1)/3.As long as the number of failed nodes does not exceed this tolerance value,the system’s data can be trans?mitted once the correct consensus has been reached,which can effectively guarantee the credibility of the data.
2) Privacy:Privacy is extremely important to the system.If a user’s private information is leaked,this may result in enor?mous losses.Our system uses private blockchain technology;thus,devices will be authenticated by blockchain,and data will be stored in the blocks in the form of transactions.A block cannot be tampered with or deleted,thereby guarantee?ing the undeniability and confidentiality of the data.Our pro?posed blockchain-based CH selection algorithm does not re?quire the intervention of a trusted third party,thereby ensur?ing the robustness and privacy of the system.
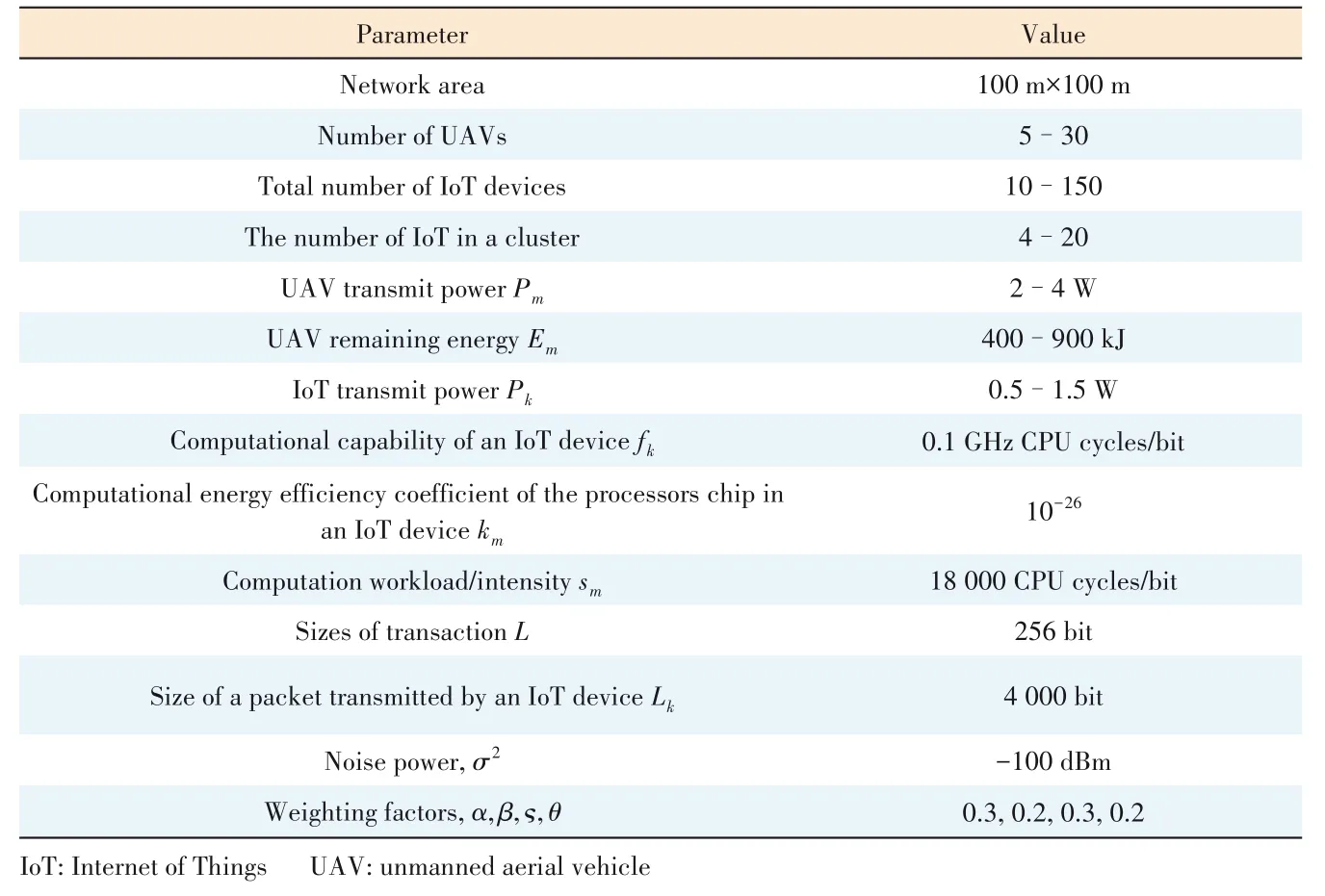
▼Table 1.Simulation parameters
4.2 Analysis of Energy Consumption of IoT Devices
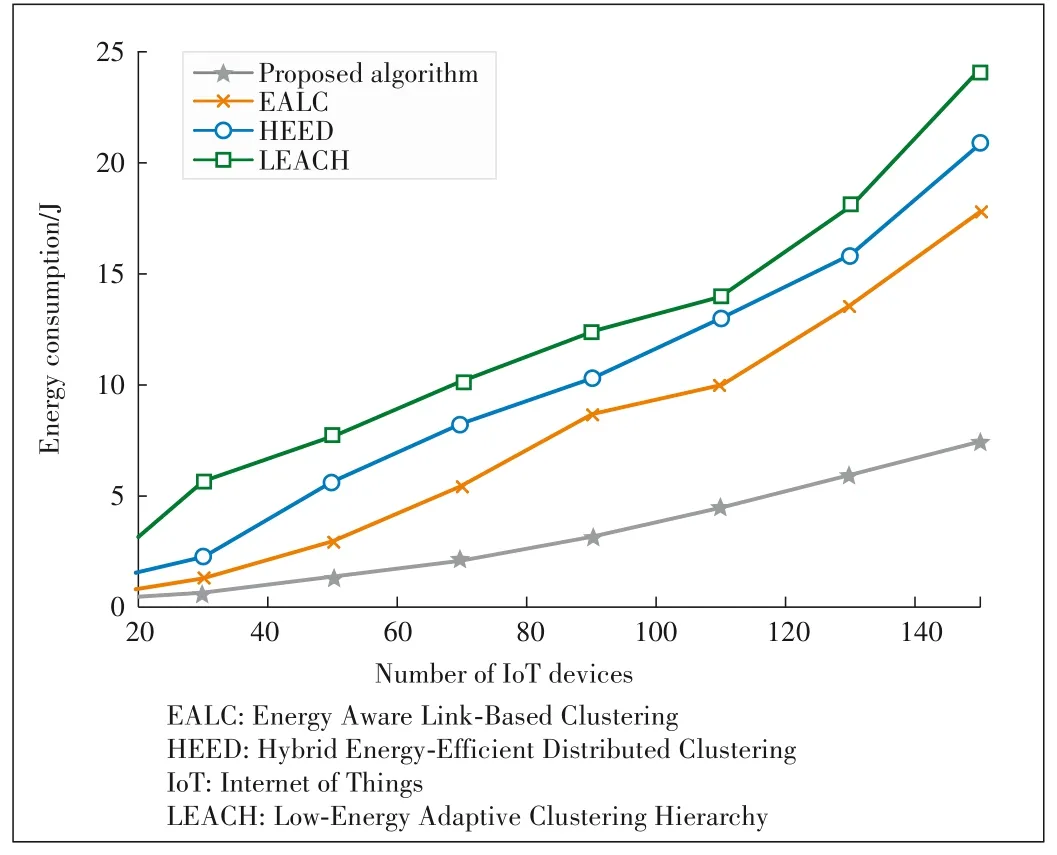
Fig.4 plots the energy consumption versus the number of IoT nodes for the various CH selection algorithms.The num?ber of UAVs is fixed at 6.From Fig.4,it can be seen that our proposed strategy achieves the minimal energy consumption compared with the other existing CH algorithms.Meanwhile,as the number of IoT devices increases,the gaps between our proposed algorithm and the other existing algorithms become larger.This gap enlargement occurs because the average dis?tance between the IoT devices and the UAVs is small and the uplink transmission between the IoT devices and the UAV CHs can take advantage of the LoS channel environment in our proposed algorithm.Therefore,our proposed algorithm in?curs significantly less energy consumption for communication than the other schemes do.Moreover,compared with the typi?cal random selection algorithms LEACH and HEED,which se?lect CHs by means of multiple votes and therefore cause the IoT devices to consume more energy,our proposed algorithm needs each device to vote only once;hence,the energy con?sumed to reach consensus within an IoT cluster is reduced.
4.3 Analysis of Average Secrecy Rate
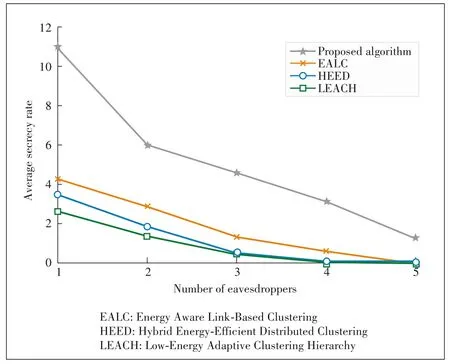
Fig.5 shows the average secrecy rates achieved with the different CH selection algorithms versus the number of eaves?droppers.The number of UAVs is fixed at 6,and the number of IoT devices is 50.The figure shows that as the number of eavesdroppers increases,the average secrecy rate decreases.The presence of more eavesdroppers will cause the eavesdrop?ping rate for an IoT cluster to increase,Hence,the secrecy rate of the IoT cluster will inevitably decrease.As shown in Fig.5,the average secrecy rate of our proposed algorithm is significantly better than those of the other existing CH algo?rithms.This is because the distance and transmit power of each UAV are considered in our proposed algorithm.In this way,both the legitimate transmission rate and the secrecy rate of the IoT clusters can be increased.
4.4 Analysis of the Maximal Number of Packets received by BS
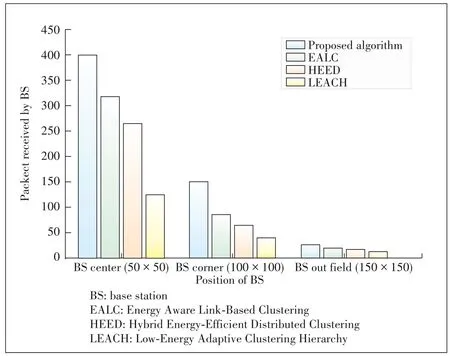
For 150 IoT devices and 6 UAVs,Fig.6 analyzes the num?ber of data packets sent by the IoT devices and received by the BS.We compare the maximal numbers of data packets that the BS can receive at three typical locations:the center of the IoT network,the corner of the IoT network,and the outside of the IoT network.Our proposed algorithm performs signifi?cantly better than the other algorithms in terms of this metric.This is because the maximal number of data packets received at the BS strongly depends on the energy of the CHs and IoT devices.Less energy consumption of the IoT clusters will lead to a longer lifetime of the IoT network,and hence,more data packets can be transmitted in the system.Our proposed algo?rithm can reduce the energy consumed by the IoT devices for communications,including data transmission,data reception,and data processing.Moreover,the remaining energy of the UAVs is also considered in our proposed CH selection algo?rithm.Consequently,the proposed algorithm can prolong the lifetime of the system by reducing the probability of UAV CH breakdown.Thus,the number of data packets received by the BS increases.
▲Figure 4.Energy consumption versus the number of IoT devices
▲Figure 5.Average secrecy rate versus the number of eavesdroppers
▲Figure 6.Packets received by BS versus different positions of BS
5 Conclusions
In this paper,we propose a novel UAV CH selection algo?rithm for IoT clusters based on blockchain technology.Our proposed algorithm considers the combined effect of the dis?tances between the IoT devices and the UAVs,the distances between the UAVs and the BS,the maximal transmission pow?er of the UAVs,and the remaining energy of the UAVs;it has the flexibility to assign different weights to these different con?tributing factors.Each IoT device votes for its optimal UAV through our proposed CH selection algorithm,and then,all IoT devices in a cluster use blockchain technology to achieve consensus to ensure the correctness and security of the vote data.The UAV with the most votes among the devices in an IoT cluster will act as the CH to serve the IoT cluster.Simula?tion results illustrate the system performance that are com?pared with corresponding results of the existing algorithms,such as LEACH,HEED and EALC.The simulation results show that our proposed algorithm outperforms the existing al?gorithms in terms of the energy consumption of the IoT clus?ters,the average secrecy rate of the IoT clusters and the maxi?mal number of data packets received by the BS.
- ZTE Communications的其它文章
- Editorial:Special Topic on Energy Consumption Challenges and Prospects on B5G Communication Systems
- Adaptability Analysis of Fluctuating Traffic for IP Switching and Optical Switching
- Integrating Coarse Granularity Part-Level Features with Supervised Global-Level Features for Person Re-Identification
- Next Generation Semantic and Spatial Joint Perception
——Neural Metric-Semantic Understanding - Kinetic Energy Harvesting Toward Battery-Free IoT:Fundamentals,Co-Design Necessity and Prospects
- Green Air-Ground Integrated Heterogeneous Network in 6G Era

