D-S Evidence Theory Based Trust Ant Colony Routing in WSN
Ziwen Sun*, Zhiwei Zhang, Cheng Xiao, Gang Qu
1 School of Internet of Things Engineering, Jiangnan University, Wu’xi 214122, China
2 Engineering Research Center of Internet of Things Technology Applications Ministry of Education, Wu’xi 214122, China.
3 Department of Electrical & Computer Engineering and Institute for Systems Research, University of Maryland, College Park, 20742, USA
* The corresponding author, email: sunziwen@jiangnan.edu.cn
I. INTRODUCTION
Security is the most basic and critical content in all kinds of network research, such as wireless mesh networks[1], underwater sensor networks[2], homogeneous wireless sensor networks[3], and social networks[4]. Especially, with the wireless sensor networks have been widely applied in industrial fields[5-8],the routing security of WSN is becoming an urgent problem needed to be resolved [9-10].The traditional cryptography technology based network security mechanisms are effectively used to resist the external attacks [11-16], and some new technologies have been researched to make sure the data security in storage [17-19]. However, these methods can’t effectively solve the threats coming from internal attacks made by malicious nodes or nodes’ sel fish behaviors. Aiming to resist the internal attacks,some of trust mechanisms have been established to improve the security and the reliability of WSN routing [20-21].
Trust models for WSN security have been studied with different theory and technology.The main approaches include the weighted average method [22], the classical probability model based method [23], the fuzzy inference method [24-25], the intelligent algorithms based method [26] and D-S theory basedmethod [27-29]. The simple weighted average method can’t be able to handle with the indirect trust relationship between nodes due to its hard to re flect the subjective uncertainty. The probability theory based method can’t reflect the real trust state of nodes due to the subjective assuming of either a prior knowledge or a probabilistic model of random distribution.The Fuzzy inference method is hard to popularize due to the membership functions relying on the practical application. The intelligent algorithms based method is mostly used as an auxiliary tool for optimization even though it provides a new direction for trust mechanism.
This paper proposes a trust ant colony routing algorithm by introducing a node trust evaluation model based on the D-S evidence theory into the ant colony routing protocol to improve the security of wireless sensor networks.
The trust based secure routing has become a hot research area in fields of WSN and security. These studies fall into two research directions which are the secure routing based on improving traditional rout algorithms [30-33]and the secure routing based on intelligent algorithms [34-38]. In [30], a trust model was constructed with the characteristics of lightweight and high ability to resist attacks which can oppose trust models, and a QoS routing framework named as A Trust-Aware Secure Routing Framework (TSRF) was built to improve the security of the network and reduce the routing overhead by combining the trust model and the theory of semiring. In [31], a trust evaluation model was proposed by adopting the D-S evidence theory for wireless mesh networks, and a trust routing protocol named as Trust Ad-hoc on-Demanding Distance Vector (T-AODV) was obtained by improving the security performance of the traditional reactive routing protocol Ad-hoc on-Demanding Distance Vector (AODV). In [32], a dynamic trust prediction model was presented by using the extended fuzzy logic rules for analyzing the nodes’ behaviors to evaluate the trustworthiness of nodes to reduce the hazards from malicious nodes, and the Trust-based Source Routing protocol was created to provide a flexible approach to choose the shortest route meeting the security requirement of data packets transmission by integrating the trust predication model into the Source Routing Mechanism. In[33], a trust-based QoS model was proposed to estimate the trust degree between nodes by considering the direct and indirect neighbors’recommendation values, and a trust-based QoS routing algorithm called the Trust-based Qos Routing (TQR) was built through considering the trade-off between the trust degree and the link delay. In [34], based on the ant colony, a trust self-organized routing algorithm named the trust ant clone optimization (TrACO)reasonably evaluated direct and indirect trust values of nodes by using a Bayesian method in the delay tolerant network, and provided a reliable routing protocol with high ability against the nodes’ selfish behaviors. In [35],a secure routing algorithm was proposed by introducing node trust value into pheromone computation of ant colony routing to overcome the problem of node energy depletion caused by internal attacks. In [36], an adaptive security routing protocol was proposed to improve the data transmission rate and the safety of the WSN routing by adding a trust threshold into the ant colony algorithm and using the encryption security mechanism. In [37],a trust routing model named as bio-inspired trust and reputation model for Wireless Sensor Networks (BTRM-WSN) firstly introduced the concept of trust into the ant colony algorithm.In [38], the BTRM-WSN model was further extended to enhance the efficiency and the scope by adding a interactive multiple ant colony optimization method into the evaluating of nodes and routing paths.
This paper takes advantages of both the D-S evidence theory and the ant colony routing algorithm to enhance the security level of routing and the energy efficiency in WSN.The D-S evidence theory and the ant colony routing algorithm have numerous advantages to establish a trust model: (i) The D-S evidence theory can provide a strong guarantee for the expression and computing of uncertainty, which can not only directly express the uncertainty but also shrink assumptions set by accumulating evidences without the prior distribution. (ii) The combination rule of D-S evidence theory is effective in integrating all kinds of uncertainty information to make right decisions. (iii) The colony algorithm has the excellent ability of fast convergence, global optimization and self-adaptation. A trust evaluation model is established based on the D-S evidence theory for WSN, and this model is further introduced to an ant colony routing algorithm to improve the security of WSN routing. Simulations conducted by using the network simulator NS2 [39] show that the proposed method can achieve a better performance in terms of the packet loss rate, the average end-to-end delay, the route discover time, the throughtput, the routing overhead and the average energy consumption. The packet loss rate and the end-to-end delay do not rapidly deteriorate as the number of inside malicious nodes increasing, and the throughtput, the routing overhead and the energy consumption also keep in a good level.
The rest of this paper is arranged as follows. Section 2 introduces the establishment of nodes trust recognition framework and the trust evaluation model based on the D-S evidence theory. Section 3 elaborates the computation of nodes’ trust, including the direct trust and the indirect trust, and the synthesis of overall trust. In Section 4, on the basis of the proposed trust evaluation model, a trust based ant colony routing algorithm is designed by integrating the trust evaluation model into the ant colony optimization algorithm. In Section 5, the simulation is conducted using NS2 to indirectly evaluate the security issue in terms of keeping the network’s performance under the inside attacks from malicious nodes. Finally, the conclusions are made in Section 6.
II. THE D-S EVIDENCE THEORY BASED TRUST EVALUATION MODEL
2.1 The D-S evidence theory model
In the D-S evidence theory, the framework of discernment (FOD) Ω is defined as a set of hypotheses which consists n mutually exclusive and exhaustive propositions providing the evidences. The power set 2Ωincludes all the subsets of Ω, which can be taken to represent propositions concerning the actual state of the system.
There are some important de finitions of the basic probability assignment function (BPA)m(A) on 2Ω: 2Ω→[0,1], the belieffunction Bel(A): 2Ω→[0,1], and the plausibility function Pl(A): 2Ω→[0,1], which satisfying the following equations:
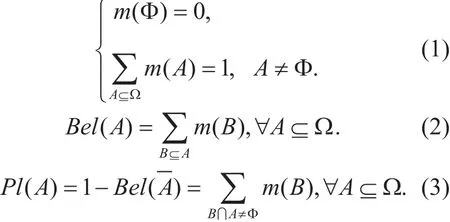
Where m(A) expresses the proportion of all evidences supporting the proposition A, a particular element of Ω belongs to the set A.Especially, the A satisfying m(A)>0 is called a focal element. The belieffunction Bel(A)represents the inevitability and signifies the total degree of believing A to quantify the strength of the belief that A occurs, forming a lower bound. The plausibility function Pl(A)represents the total belief degree related to the probability of A, forming a upper bound.
If there are n completely exclusive evidences over the FOD Ω , the BPAs of these evidences can be termed as m1(A),m2(A),...,mn(A)respectively. According to the Dempster’s rule of combination, the combination of beliefs(called joint mass) m(A) can be obtained based on these BPAs, which meet the following combination rule:
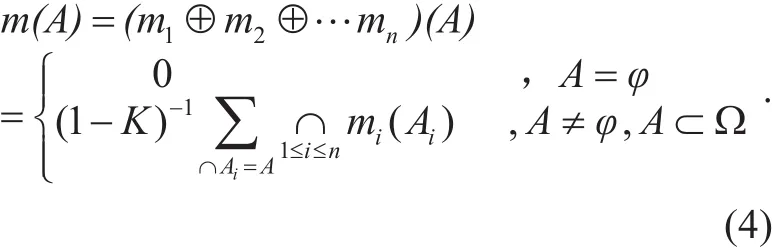
2.2 The trust evaluation model
In our problem, a degree of confidence is a trust of an evaluated node estimated by an evaluating node according to the evaluated node’s behaviors, and an ideal trust relationship should always take both the direct trust value and the indirect trust value recommended by other nodes. In a distributed WSN, an evaluated node’s direct trust information and indirect information are obtained through monitoring behaviors between adjacent nodes,like a watchdog. As shown in figure 1, the trust evaluations from node i to node j include the direct evaluation from node i and the indirect evaluations from the third party nodes k1,k2, k3 and k4, namely a recommendation trust,each of which forms a recommendation trust chain.
The trust evaluation problem can be modeled as a D-S evidence theory model. A trust evaluation model based on the D-S evidence theory is constructed and shown in figure 2.

Fig. 1. The relationship of trust evaluation between nodes.
In the problem of trust evaluation of a node, the source of the trust evidences can be obtained from the monitoring values of the behaviors of the evaluated nodes. Four main trust evidences are chosen as the evidence sources from the received packets rate,the sending packets rate, the packets forwarding rateand the degree of packets consistency, which depend on the history interactions between neighbor nodes,flag is 1 or 0 represents success or failure respectively. All of the four evidences are independently obtained from the monitoring.
The frame of discernment is de fined as Ω={T,-T}, where T and -T represent the trusted and distrusted states of one node respectively.As a result, 2Ω={Φ,{T},{T,-T},{-T}}, where Φ, {T}, {-T}, {T,-T} represent the empty set,the propositions of nodes’ ‘Trust’, ‘Distrust’and ‘Uncertain’ respectively. Therefore,Bel(T) = m({T}), Pl(T) = m({T}) + m({T, ?T}), especially, Bel(Φ)=0, Bel(Ω)=1. The element number in the frame of discernment has relationship with the number of the focal elements, which has been described that the possible number of focal elements is 2n?1 corresponding to the element number n in the frame of discernment[40]. In this paper, the value of n is two, therefore, focal elements is three. Consequently, the total focal element number of all nodes is the triple of the nodes’number, which does not lead to the problem of the focal elements explosion existing in many other using of D-S combination rule.
The single direct trust value and the multiple indirect trust values are calculated, updated and processed independently and respectively.The integrated trust value can be obtained both from the direct and the indirect trust values through the D-S combination model and the evaluation function method.
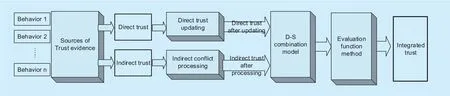
Fig. 2. The trust evaluation model based on the D-S evidence theory.
III. TRUST COMPUTATION
3.1 Direct trust and its updating rule
According to the history of the sending and receiving behaviors among grouping nodes, the nodes’ trust degree can be measured.
The current direct trust vector CDTi,jobtained from the behaviors of node j is descripted according to the trust monitoring mechanism among nodes as the formula (5):

Where functions F1and F2are chosen in advance according to the specific assignments of the network, ω1, ω2, ω3and ω4are the weights of evidence sources satisfyingandrepresent three kinds of BPA of trust, distrust and uncertain respectively.
To evaluate the history of the behaviors of node j, the direct trust vector DTi,jis updated relying on the history interactions of two sequential cycles according to the formula (6):

Where CDTi,jand HDTi,jis the current and the latest cycle trust value of node j evaluated by node i respectively. The parameter β is the adaptive time factor used to weight the history experience against the current information. To keep preferably dynamic, β is an adaptive value as formula (7):

3.2 Indirect trust and con flict preprocessing
3.2.1 Indirect Trust Computing
Due to the transitivity of trust relationships between nodes, an evaluating node can obtain the indirect trust value of an evaluated node through different recommendation paths formed by different third party nodes, which depend on nodes’ distribution and transmission radius. To avoid the trust recycle recursion and reduce the network communication payload,the third party nodes are limited to the space covered by the common communication radius of the evaluating and the evaluated nodes,like the nodes k1, k2, k3and k4in Figure 1.
Given the recommended trust valuefrom the recommendation path k1, the vector of, DT and DT can be representedi,k1k1,jas follows:
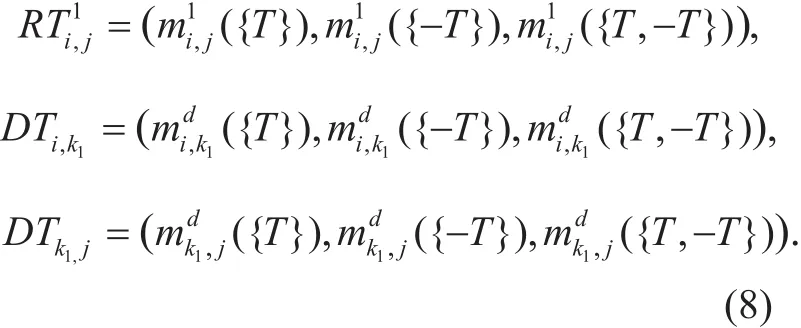
Where,
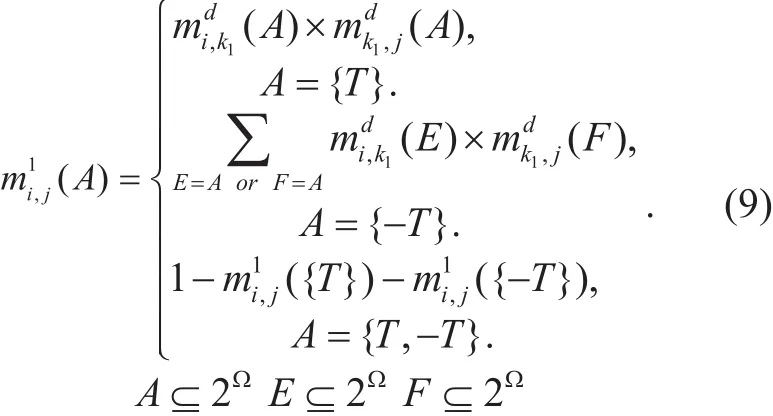
3.2.2 Con flict preprocessing
Assume s recommended trust values of j are provide to i according to the trust transitivity:
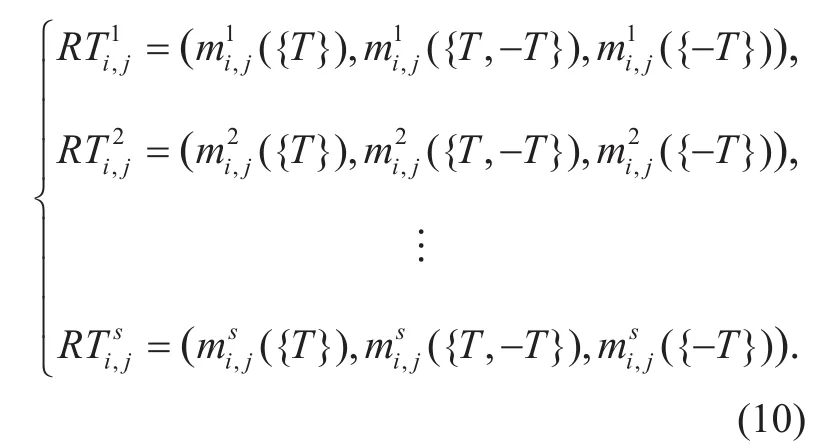
The con flict evidences are main caused by the malicious nodes offering false recommendations, the con flict evidences will result in an incorrect judgment by using D-S combination rule. In order to avoid a counter-intuitive result in case of con flict evidences caused by the malicious nodes offering false recommendations,the consistent intensity[41] is adopted in the node trust evaluation model to adjust weights of recommended trust values.
The consistency intensity Iu,vbetweenandis de fined by the evidence distance function to measure the similarity of two recommendation evidences, shown as formula(11):
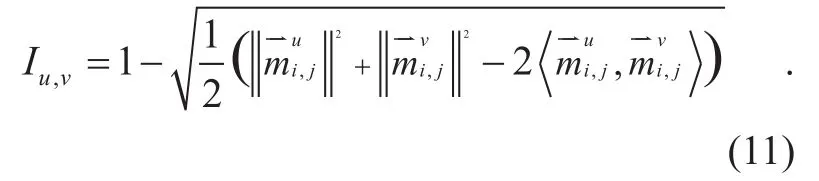
Where u=1,2,…,s ; v=1,2,…,s ;is the innerThe big distance between two recommended trust evidences will reduce the consistency intensity. The lower the consistency intensity Iu,vis, the more probably a false trust recommendation may occur.Therefore, a big consistency intensity is expected.
The matrix of consistency intensity consisting of all the recommended trust values can be directed from formula (11) :
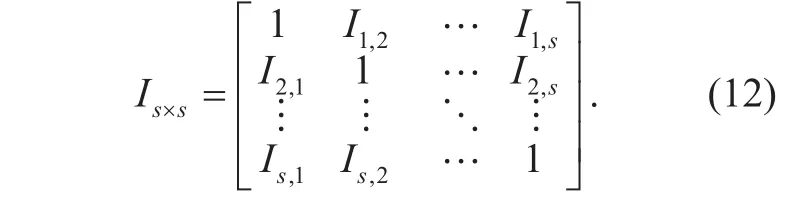
The totally consistency intensity of recommended trustis defined as the normalization of the u-th row summation[42], shown as formula (13):
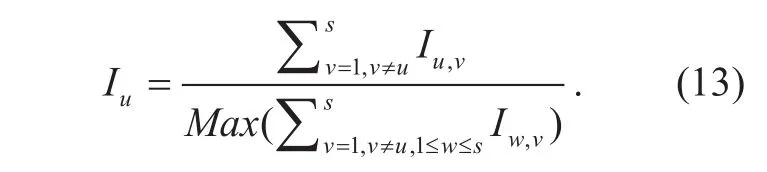
The belieffunction of recommended trust evidences is modi fied by Iuas formula (14):
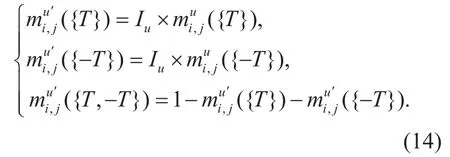
Where u=1,2,…,s .
Finally, the recommended trust is described using the modi fied vector as formula (15):
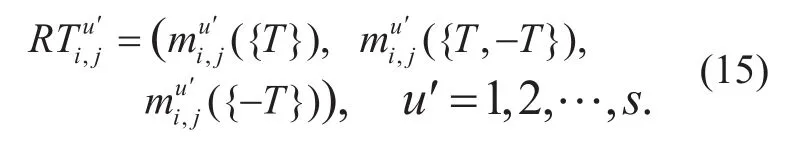
3.3 Integrated trust
The combination of beliefs vector ITi,jof all evidences will be obtained by the evaluating node i to integrate the evaluated node j’s direct trust values as (6) and the preprocessed indirect trust values as (15) according to the combination rule formula (4), shown as formula(16):

The combined beliefs are independent to each other for each of the evidences is independently obtained. However, the final judgment is not decided by ITi,j.
The final judgement is determined by the evaluation function. The evaluation function is a kind of probability function that is deduced from the belieffunction and the plausibility function. The evaluation function can be used as both the imprecise measurement and the trust estimation method of knowledge, therefore the evaluation function is applied as the judgement to obtain a final evaluation trust value of a node being closer to the real standard.
The definition of evaluation function [38]is introduced here: Assume that in the finite recognition framework of Ω, the evaluation function of any proposition A, which meets the constraint A ? X, is defined as formula(17):
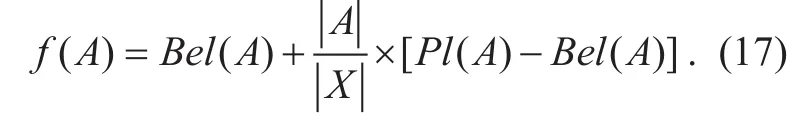
Where Pl(A)-Bel(A) represents the uncertainty degree of proposition A, |A| and |X| represent the number of elements in A and X respectively.
The evaluation function of the evaluated node j can be calculated according to the formula (17) and the combination of beliefs vector ITi,jin formula (16), as formula (18):
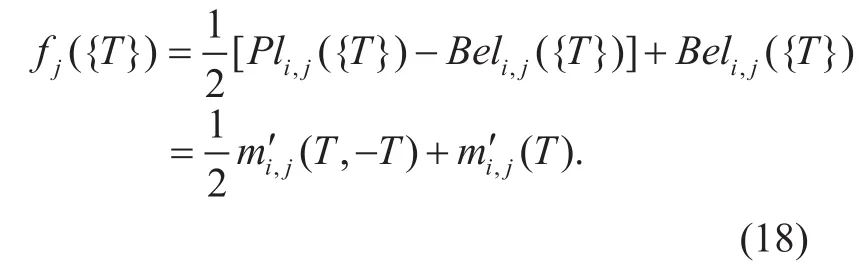
Where Beli,j() Pli,j() are computed using formula (2)(3) with the modi fied vector as formula (15).
The decision judgment rule:If the conditions described in formula (19) are all satisfied, the evaluated node j is regarded as trustful, otherwise, the node j is regarded as trustless.
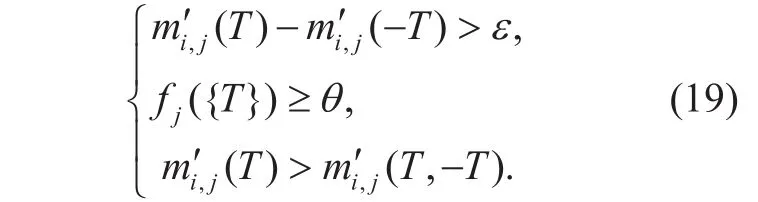
Where θ (0≤θ≤1) is the threshold value to measure the evaluation function, and ε is a minimal positive value.
IV. TRUST ANT SECURE ROUTING
The secure and reliable WSN routing will be built to resist internal malicious attacks by combining the ant colony optimization framework and the trust evaluation model.The main advantages are that of the D-S theory’s high inferential capability and the colony algorithm’s excellent ability of fast convergence, global optimization and self-adaptation through accumulating knowledge by reinforcement learning approach. The process of routing algorithm consists of multiple rounds of cycle, and each round of cycle includes three steps including the routing discovery, the pheromone updating and the routing maintenance, as shown in figure 3.
4.1 Routing discovery
A source node would check the routing table to decide whether to start a routing discovery process before sending data packets to the destination node. If there is no satisfactory and unexpired route to the destination in its routing table, a source node generates a certain number of forward ants to search for a appreciate route to the destination. Each of the forward ants (the intermediate nodes) makes a decision for selecting the next forwarding node at each round of cycle according to a probabilistic decision rule as formula (20):
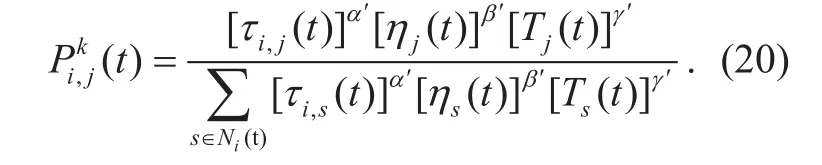
Where the important parameters, which are considered as the heuristic function of candidate next node j, include the pheromone information τi,j(t), the remaining energy ηj(t)and the trust value Tj(t ) at time t. τi,j(t) is the link pheromone value between node i and node j;E(t) denotes the residjual energy information of node j and Einitdenotes the initial energy value; Tj( t)=fj({T })denotes the evaluation function value. And α′, β′ and γ′ are weight coefficients related to each single element; Ni( t ) represents the neighbor set of node i.
Each intermediate node u must update the information carried by the forward ant according to the rule shown in formula (21) before its forwarding process:
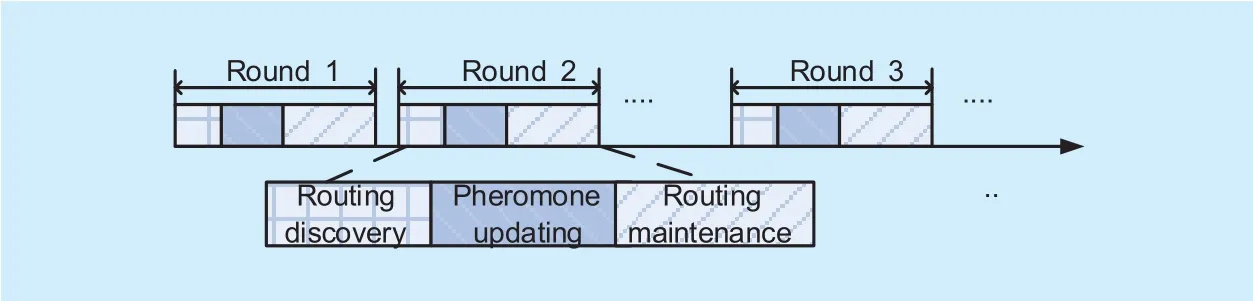
Fig. 3. Process of routing algorithm.

where, Eminand Tminrepresents the minimum residual energy and the minimum trust value among the passed-by nodes at time t or t-1 respectively .
4.2 The pheromone updating
The pheromone will be updated by both the forward ants and the backward ants when they past the routing link. The forward ants complete the local pheromone update, while the back ants complete the global pheromone update.
Whenever a forward ant passes by the routing link (i, j), there is a local increasing of pheromone and the response from the local evaporation of pheromone. The local pheromone update is completed by the k’th forward ant according formula (22):

Where ρ is a local evaporation coefficient,and Δτi,j(t) is a local increasing of pheromone caused by the k’th forward ant shown as formula (23):
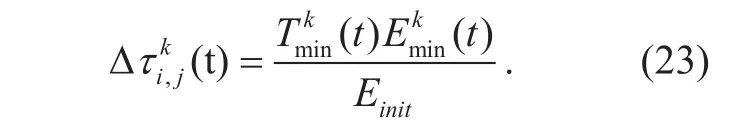
As soon as a forward ant reaches the destination, it is changed to be a backward ant which immediately returns to the source node along the reverse routing path of its’ corresponding forward ant. The global pheromone update is completed by the backward ant when it passes by a rout link on the reverse routing route. The global pheromone update is the contribution of all of the ants according to formula (24):
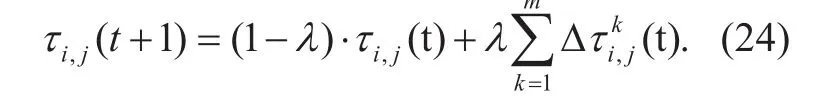
Where m is the number of forward ants reaching the destination, λ is a global updating coefficient.
When all of the backward ants reach the source node, the source node will update the routing table and sends the cache data packets to the destination node.
4.3 Routing maintenance
Each node’s behaviors in WSN are monitored by its neighbor nodes according to the trust monitoring mechanism relying on the proposed trust model when the data packets are passed among the nodes, meanwhile each node’s trust value is periodically updated with a cycle Td. According to the decision judgement rule as formula (19), the evaluating node updates its neighbor’s neighbor table by adding new trustful nodes or deleting malicious nodes.
4.4 The main algorithms
The main algorithms for the Route discovery and Pheromone updating are described in algorithm 1.
V. SIMULATION AND RESULTS
5.1 Simulation scene
The simulations are conducted based on the platform of windows xp+cygwin2.738+ns2.35.All the simulations are conducted within a rectangular field of 1000 m×1000 m with 50 nodes randomly distributed. 10 pairs of nodes are randomly selected as source nodes and destination nodes for each simulation, while a certain number of nodes are selected as the malicious nodes to simulate black hole attack.The settings of speci fic parameters of nodes are shown in Table I, and the simulation scenario with 15 malicious nodes is shown in figure 4. For the black hole attack, the malicious nodes trick other nodes around to send packets to them and deliberately lose the packets at the same time. For the main in fluence of black hole attack is packets sending, receiving and forwarding, the weights of evidence sources ω1, ω2, ω3and ω4in formula (5) are selected as {0.3,0.3,0.3,0.1} in the simulation tests.The parameters of the proposed routing algorithm are shown in Table II by taking both the security and the network performance of WSN into consideration. The values of nonkey parameters βs, βc, θ, Td, ρ and λ are firstly set according to the basic constraint conditions. The values of βsand βcsatisfy the constraint of 0≤βs≤0.5≤βc≤1 to ensure the update processes of the direct trust values keep in a dynamic balance. The value of θ is set as 0.5 which is the threshold level of security requirements, the larger value will lead to excessive trust nodes being incorrectly judged as distrust, and the smaller value will lead to the number of malicious nodes increasing. The values of Td, ρ and λ may be finetuned according the practical simulation tests.The values of key parameters α′, β′ and γ′ will be set to satisfy the constraint among the values of nodes’ pheromone, energy, and trust. A good constraint can be obtained with α′+β′+γ=1 [35]. As an important security factor, a big value of γ′ is set to satisfy γ′>α′, γ′>β′ to ensure the security of nodes.
5.2 Results and analysis
The simulation tests are conducted to compare the proposed trust routing model with the energy-efficient ant-based routing algorithm( EEABR)[43] and its’ improved routing algorithm Improved Energy-Efficient Ant-Based Routing Algorithm (IEEABR)[44] to verify the performance of the proposed trust routing model. In order to compare the performances of the three routing algorithms, five kinds of simulation scenarios are set up with different number of malicious nodes such as 0, 5, 10,15, 20 and 25 respectively.
The security issue can be indirectly evaluated by observing the outcome of the performances of the network through varying the number of malicious nodes. WSN will be subjected to several common attacks, such as black hole attack, selective forwarding attack,wormhole attack, sinkhole attack, acknowledgement spoo fing attack, Sybil attacks, HELLO flood attack, etc[45]. The internal nodes of WSN are vulnerable to the behaviors of malicious nodes with the above different attacks,all of these behaviors will destroy the routing mechanism, reduce the network stability, and affect the network performance such as packet loss rate, end to end delay, throughput and so on. Therefore, six kinds of performance metrics of network, which are the packet loss ratio, the average end-to-end delay, the route discovery time, the throughput, the routing packet overhead and the average energy consumption, are used to estimate the efficiency of the proposed security routing in keeping the network performance.

?
?
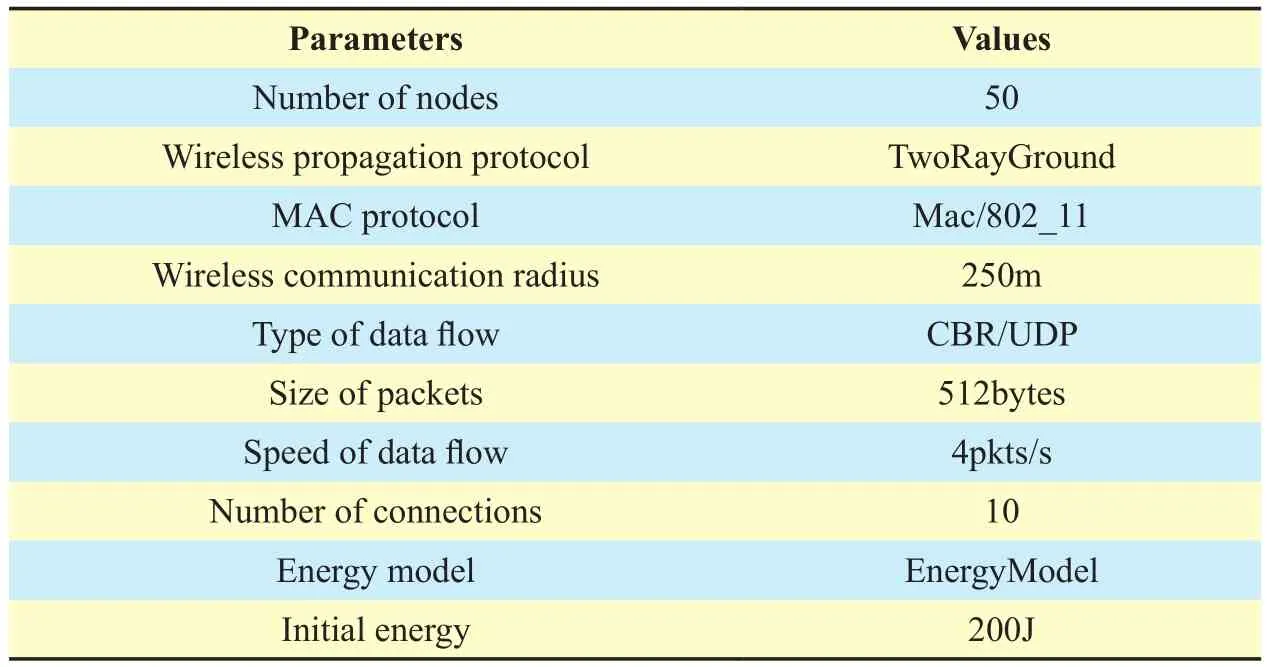
Table I. The settings of parameters of nodes
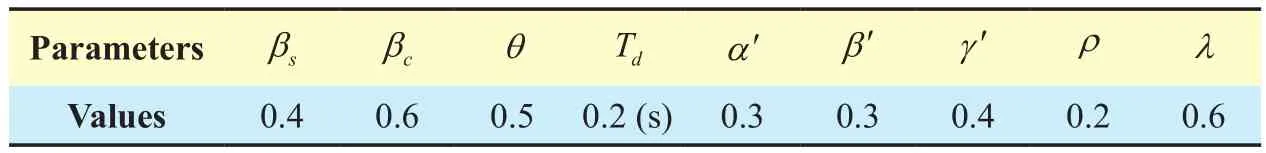
Table II. The parameters of algorithm
Fig. 4. Simulation scenario of 15 malicious nodes.
The simulation results are shown in Table III. From Table III, the analysis can be concluded.
(1) Packets loss rate
When there is no malicious nodes, the loss rates of all the three routing algorithms keep at a low level. However, as the number of malicious nodes increases, the loss rate of each algorithm growths with different speed.
When the number of malicious nodes varies from 0 to 25, the loss rate of the proposed routing algorithm increases from 5.1% to 19.8% with a variation range of 14.7%; whereas the loss rates of EEABR/IEEABR rose from about 4.9%/4.1% to 35.2%/34.6%, and the variation ranges are over 30% which are much larger than that of the proposed routing algorithm.
The simulation results prove that the proposed trust routing algorithm has more power to resist the malicious attacks (black hole attack) than EEABR and IEEABR. The better performance is due to the most trusted nodes being selected to establish the rout by evaluating the nodes’ malicious behaviors with the trust evaluation model, consequently, the packet loss rate is reduced and the ability of the intrusion tolerance of the network is improved.
(2) Average end-to-end delay
The average delays of all the three algorithms increase with the add of malicious nodes, this is because more malicious nodes will result in a long end-to-end delay for retransmiting more packets to the destination.
The average delay of the proposed algorithm is not lower than that of EEABR andIEEABR when the number of malicious nodes is less than 10. This phenomenon is due to the time costing for computing and updating the trust values of neighbor nodes even though there are few malicious nodes existing.
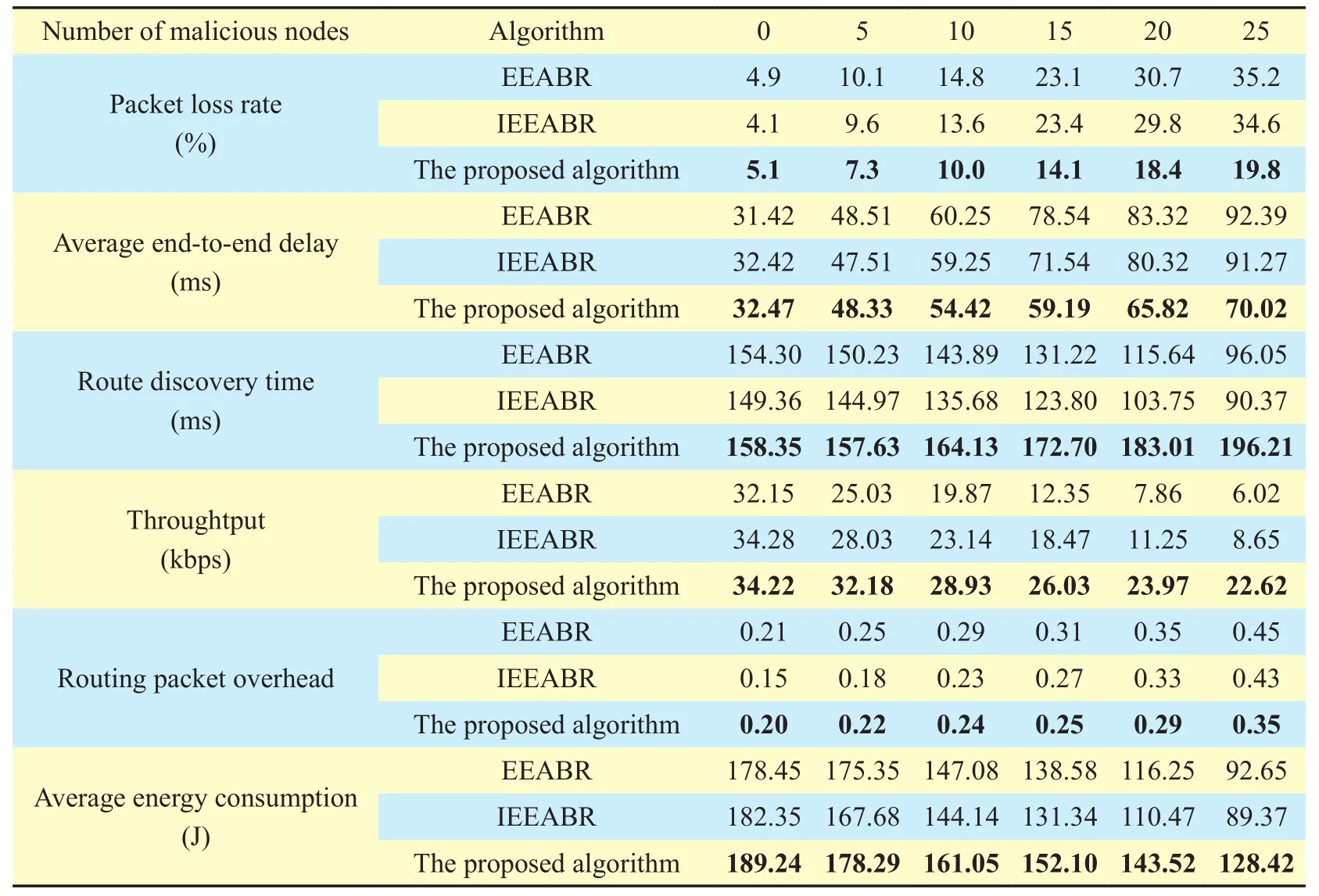
Table III. Results of performances
The average delay of the proposed algorithm is lower than that of EEABR and IEEABR when the number of malicious nodes is over 10. In EEABR and IEEABR, the more malicious nodes existing will result in more packets being lost, and which will further increase the number of packets to be retransmitted and prolong the end-to-end delay. Whereas, in the proposed trust routing algorithm, the malicious nodes are efficiently monitored and isolated from the routing path to improve the reliability of packets’ delivery. Therefore, the average delay is much less than that of other two algorithms, this effect is more obvious when the number of malicious nodes increases. It is obvious that the use of D-S evidence theory does not increase the end to end delay too much no matter there are malicious nodes or not. Even more, when the number of attack nodes increasing, the delay is reduced compared with the other two algorithms, which proves that the focal elements explosion problem in this algorithm does not exist.
(3) Route discovery time
With the increasing of number of malicious nodes from 0 to 25, the route discovery time decreases about 60ms in EEABR and IEEABR, reversely, the route discovery time of the proposed algorithm increases from 158.35ms to 196.21ms.
This kind of phenomenon implies that the EEABR and IEEABR cannot recognize the malicious nodes with the lack of security mechanism. Consequently, the false routing response messages being received, which come from black hole nodes to claim that they have the route to the sink node, will result in decreasing the route discovery time in EEABR and IEEABR. On the contrary, when the number of malicious nodes increases, the proposed algorithm can avoid the black hole nodes and refuse the false routing response messages due to each node need to be evaluated its trust, therefore the more time will be taken to identify the malicious nodes to find a security routing path.
(4) Throughtput
The throughtputs of the three algorithms reduce with different speed as the number of malicious nodes increases.
With the number of the malicious nodes increase from 0 to 25, the throughtputs reduces from 32.15kbps/34.28kbps to 6.02kbps/8.65kbps in IEEABR/EEABR. The main reason it that the increase of black hole nodes makes the network routing dif ficult to remain stable, which results in the packet loss and further results in the decrease of throughtput.
At the same situation, the throughtputs reduces from 34.22kbps to 22.62kbps in the proposed algorithm, which changes far slowly than that of EEABR and IEEABR. The main reason is that the proposed routing algorithm can effectively resist the malicious attacks to avoid a large number of packets being lost while EEABR and IEEABR have no such ability.
(5) Routing packet overhead
The routing packet overheads of all of the three algorithms gradually increase as the number of malicious nodes increases. When the number of malicious nodes is less than 10,the routing packet overhead of the proposed algorithm is lower than that of EEABR but slightly higher than that of IEEABR. In the case of malicious nodes over 10, the routing packet overhead of the proposed algorithm increases slowly than that of the EEABR and EIIABR when the number of malicious nodes increases. In the most extreme cases of 25 malicious nodes, the routing packet overhead of the proposed algorithm is 0.35 compared with 0.45 and 0.43 corresponding to EEABR and EIIABR.
The difference is due to whether utilizing the trust security model or not. The proposed algorithm needs extra routing control packets to maintain trust tables of nodes through maintaining and updating the direct trust values and indirect trust values. Therefore, when there are few malicious nodes in the network, the proposed algorithm’s routing packet overhead is no better than that of other two compared algorithms. With the increasing of malicious nodes, there are massive loss packets which lead to a routing overhead due to the absence of trust security model against the malicious nodes’ attack in EEABR and IEEABR algorithms. On the contrary, the proposed algorithm can identify the inside malicious nodes’attacks by using the nodes’ trust model to avoid malicious nodes in the phrase of routing discovery, consequently, the routing overhead can hold on a relative low level.
(6) Average energy consumption
The energy consumptions of all the three algorithms descend along with the increasing of malicious nodes. The reason is that the energy consumption is mostly caused by packets transmission, therefore the energy consumption will decrease with packets lost due to the attacks from malicious nodes
Compared to EEABR and IEEABR, the energy consumption of the proposed algorithm is higher. As the number of malicious nodes varies from 0 to 25, the consumption of energy of the proposed algorithm changes from 189.24J to 128.42J with the variation of nearly 60.82J,while that of the EEABR and IEEABR changes from 178.45J to 92.65J and from 182.35J to 89.37J with the decreasing amplitude are upper to 85.8J and 92.98J respectively. The reason is that both EEABR and IEEABR have no security mechanisms to monitor nodes’ behaviors, as a result, there would be more packets lost and less energy consumption when numerous black hole attack nodes exit in the network. On the contrary, the malicious nodes are monitored and isolated by the mechanism contained in the proposed algorithm to ensure the data packets transmitted in a reliable and secure way, therefore little change in energy consumption is introduced due to the number of packets loss being greatly reduced.
Even though more energy consumption will be introduced in the proposed algorithm for the using of D-S theory in security mechanism, the largest energy consumption is only 6.91J higher than that of IEEABR algorithm with zero malicious node. And with the number of malicious nodes increasing, the energy consumption will decrease down.
VI. CONCLUSIONS
The theory of D-S evidence is frequently used to resolve the uncertainty and fusion of different evidences in a complicated problem. Based on this theory, this paper establishes a trust evaluation model to estimate a node’s trust value in WSN. Furthermore, a reliable ant colony routing algorithm is proposed by considering the node trust value as the heuristic function. A reliable routing path is established for data transmission through selecting trusted node according to the nodes’ trust values stored in the routing table.
To evaluate the effectiveness of the proposed algorithm, a series of simulations are completed on NS2. The simulation results show that the proposed method can effectively monitor and isolate the malicious nodes such as black hole attacks, and it also can keep the performance of the average end-to-end delay, the throughtput and the routing packet overhead of the network in the presence of malicious nodes. The proposed secure routing algorithm outperforms the EEABR and IEEABR in keeping the performance of WSN in the case of attacks from malicious nodes,and this advantage is especially obvious when enormous malicious nodes existing in a network.
ACKNOWLEDGEMENTS
The authors would like to thank the reviewers for their detailed reviews and constructive comments, which have helped improve the quality of this paper. This work is supported by the National Natural Science Foundation of China (NSFC) under Grant No. 61373126, the Natural Science Foundation of Jiangsu Province of China under Grant No. BK20131107,the Fundamental Research Funds for the Central Universities under Grant No. JUSRP51510.
[1] P. Guo, J. Wang, X.H. Geng, et al., “A Variable Threshold-Value Authentication Architecture for Wireless Mesh Networks,” Journal of Internet Technology, vol. 15, no. 6, 2014, pp. 929-935.
[2] J. Shen, H. Tan, J. Wang, et al., “A Novel Routing Protocol Providing Good Transmission Reliability in Underwater Sensor Networks,” Journal of Internet Technology, vol. 16, no. 1, 2015, pp.171-178.
[3] S. Xie, Y. Wang, “Construction of Tree Network with Limited Delivery Latency in Homogeneous Wireless Sensor Networks,” Wireless Personal Communications, vol. 78, no. 1, 2014, pp. 231-246.
[4] T. Ma, J. Zhou, M. Tang, et al., “Social Network and Tag Sources Based Augmenting Collaborative Recommender System,” Ieice Transactions on Information & Systems, vol. 98, no. 4, 2015,pp.902-910.
[5] B. Cheng, S. Zhao, S. Wang, et al., “Lightweight Mashup Middleware for Coal Mine Safety Monitoring and Control Automation,” IEEE Transactions on Automation Science and Engineering,Vol.14, No.2, 2017, pp.1245-1255.
[6] B. Cheng, D. Zhu, S. Zhao, et al., “Situation-Aware IoT Services Coordination Platform Using Event Driven SOA Paradigm,” IEEE Transactions on Network and Services Management, Vol.13,No.2, 2016, pp.349-361.
[7] B. Cheng, X. Cheng, C. Zhang, et al., “Wireless Machine to Machine Based Mobile Substation Monitoring for District Heating System,” International Journal of Distributed Sensor Networks,Vol.2014, no.1, 2014, pp. 1-16.
[8] W.U. Xiaokun, Y. Tian, W.U. Jiyan, et al., “A Composite Service Provision Method Based on Novel Node Model in Mobile Ad Hoc Networks,”China Communications. Vol.11, No.4, 2014, pp.130-142.
[9] Z.S. Zin, N.B. Anuar, M.L.M. Kiah, et al., “Routing protocol design for secure WSN: Review and open research issues,” Journal of Network and Computer Applications, vol. 41, no. 5, 2014, pp.517-530.
[10] SURENDRAN, PRAKASH, “An ACO Look-Ahead Approach to QOS Enabled Fault-Tolerant Routing in MANETs,” China Communications, vol. 12,no. 8, 2015, pp.93-110.
[11] J. ZHOU, “Eきcient and Secure Routing Protocol Based on Encryption and Authentication for Wireless Sensor Networks,” Proc. ICAIE, 2010,pp. 406 - 409.
[12] M.S. SAHOO, M.P.K. MISHRA, R.N. SATPATHY,“Secure Routing in Wireless Sensor Networks,”International Journal of Computer Science Issues(IJCSI), vol. 9, no. 1, 2012, pp. 1-2.
[13] Y. Zhang, J. Yang, W. Li, et al., “An authentication scheme for locating compromised sensor nodes in WSNs,” Journal of Network and Computer Applications, vol. 33, no. 1, 2010, pp. 50-62.
[14] A.M. EI-Semary, “Energy-Eきcient Secure Routing Protocol Based on Roulette-Wheel and μTesla for Wireless Sensor Networks,” The Inter-national Journal of Sensor Networks and Data Communications, vol.1, no.1, 2012, pp. 1-13.
[15] N. Gui, J. Hu, Z. Chen, “A secure routing protocol and its application in multi-sink wireless sensor networks,” Journal of Networks, vol. 5,no. 5, 2010, pp. 535-542.
[16] V.T. KESAVAN, S. RADGAKRISHNAN, “Multiple secret keys based security for wireless sensor networks,” International Journal of Communication Networks and Information Security (IJCNIS),vol. 4, no. 1, 2012, pp.68-76.
[17] Y. Ren, J. Shen, J. Wang, et al., “Mutual Veri fiable Provable Data Auditing in Public Cloud Storage,” Journal of Internet Technology, vol. 16, no.2, 2015, pp. 317-323.
[18] Z. Fu, X. Sun, Q. Liu, et al., “Achieving Eきcient Cloud Search Services: Multi-Keyword Ranked Search over Encrypted Cloud Data Supporting Parallel Computing,” Ieice Transactions on Communications, vol. E98.B, no. 1, 2015, pp. 190-200.
[19] Z. Xia, X. Wang, X. Sun, et al., “A Secure and Dynamic Multi-Keyword Ranked Search Scheme over Encrypted Cloud Data,” IEEE Transactions on Parallel & Distributed Systems, vol. 27, no. 2,2016, pp.1-1.
[20] W. Fang, C. Zhang, Z. Shi, et al., “BTRES: Beta-based Trust and Reputation Evaluation System for wireless sensor networks,” Journal of Network & Computer Applications, vol. 6, no. 13,2015, pp. 1-7.
[21] S.M. Sajjad, S.H. Bouk, M. Yousaf, “Neighbor Node Trust Based Intrusion Detection System for WSN,” Procedia Computer Science, vol. 8, no.3, 2015, pp. 183-188.
[22] D.J. Wei, Z.P. Jia, X. Li, “Distributed trust model in wireless Ad Hoc networks,” Journal of Computer Applications, vol. 31, no. 1, 2011, pp. 129-132.
[23] Y. Lu, K. Lin, K. Li, “Trust Evaluation Model against Insider Attack in Wireless Sensor Networks,” Proc. 2012 Second International Conference on Cloud and Green Computing, 2012, pp.319-326.
[24] S. Sethi, S.K. Udgata. “Fuzzy-based trusted ant routing (FTAR) protocol in mobile ad hoc networks,” Proc. Proceedings of the 5th international conference on Multi-Disciplinary Trends in Arti ficial Intelligence, 2011, pp.112-123.
[25] H. Jadidoleslamy, M.R. Aref, H. Bahramgiri, “A fuzzy fully distributed trust management system in wireless sensor networks,” International Journal of Electronics and Communications, vol.9, no. 17, 2015, pp.1-10.
[26] H. Marzi, M. Li, “An Enhanced Bio-inspired Trust and Reputation Model for Wireless Sensor Network,” Procedia Computer Science, vol. 19, no.10, 2013, pp. 1159-1166.
[27] R. Feng, X. Xu, X. Zhou, et al., “A trust evaluation algorithm for wireless sensor networks based on node behaviors and ds evidence theory,”Sensors, vol. 11, no. 2, 2011, pp. 1345-1360.
[28] L. Zhang, J.W. Liu, R.C. Wang, et al., “Trust evaluation model based on improved D-S evidence theory,” Journal on Communications, vol. 34, no.7, 2013, pp. 167-173.
[29] N. Yu, X. Wang, R. Feng, et al., “Trust Management Scheme Based on D-S Evidence Theory for Wireless Sensor Networks,” International Journal of Distributed Sensor Networks, vol.2013, no. 1, 2013, pp. 130-142.
[30] J. Duan, D. Yang, H. Zhu, et al. “TSRF: A Trust-Aware Secure Routing Framework in Wireless Sensor Networks,” International Journal of Distributed Sensor Networks, vol. 2014, no. 1, 2014,pp.1-14.
[31] K. Yang, J.F. Ma, C. Yang, “Trusted routing based on D-S evidence theory in wireless mesh network,” Journal on Communications, vol. 32, no.5, 2011, pp. 89-96.
[32] H. Xia, Z. Jia, X. Li, et al., “Trust prediction and trust-based source routing in mobile ad hoc networks,” Ad Hoc Networks, vol. 11, no. 7, 2013,pp. 2096-2114.
[33] B. Wang, X. Chen, W. Chang, “A light-weight trust-based QoS routing algorithm for ad hoc networks,” Pervasive and Mobile Computing, vol.3, no. 4, 2014, pp. 164-180.
[34] H.U. Haifeng, X.G. Liu, “Trust Ant Colony Self-Organization Routing Algorithm in Delay Tolerant Network,” Journal of Nanjing University of Posts and Telecommunications: Natural Science, vol. 34, no. 2, 2014, pp. 57-64.
[35] C.F. Lai, C.F. Lai, X. Liu, et al., “Energy eきciency routing with node compromised resistance in wireless sensor networks,” Mobile Networks and Applications, vol. 17, no. 1, 2012, pp. 75-89.
[36] N.A. Alrajeh, M.S. Alabed, M.S. Elwahiby, “Secure ant-based routing protocol for wireless sensor network,” International Journal of Distributed Sensor Networks, vol. 12, no. 2013, 2013,pp.761-764.
[37] F. Gómez Mármol, G. Martínez Pérez, “Providing trust in wireless sensor networks using a bio-inspired technique,” Telecommunication systems,vol. 46, no. 2, 2011, pp. 163-180.
[38] Y. Pan, Y. Yu, L. Yan, “An improved trust model based on interactive ant algorithms and its applications in wireless sensor networks,” International Journal of Distributed Sensor Networks,vol. 4, no. 1, 2013, pp. 385-388.
[39] Leyi, Wenjing, Cong, et al., “A Sensor Anonymity Enhancement Scheme Based on Pseudonym for Clustered Wireless Sensor Network,” China Communications, vol. 9, no. 9, 2014, pp. 6-15.
[40] D.Q. Han, Y. Yang, C.Z. Han, “Advances in DS evidence theory and related discussions,” Control and Decision, vol. 29, no. 1, 2014, pp.1-11.
[41] Z.W. Sun, H. Li, Z.C. Ji, “Fusion image steganalysis based on Dempster-Shafer evidence theory,”Control and Decision, vol. 26, no. 8, 2011, pp.1-5.
[42] Z.G. Liu, Y.M. Cheng, Q. Pan, et al., “Combination of weighted belieffunctions based on evidence distance and con flicting belief,” Control Theory& Applications, vol. 26, no. 12, 2009, pp. 1439-1442.
[43] T. Camilo, C. Carreto, J.S. Silva, et al., “An Energy-Efficient Ant-Based Routing Algorithm for Wireless Sensor Networks,” Ant Colony Optimization and Swarm Intelligence. Springer Berlin Heidelberg, 2006, pp. 49-59.
[44] A.M. Zungeru, K.P. Seng, L.M. Ang, et al., “Energy Eき ciency Performance Improvements for Ant-Based Routing Algorithm in Wireless Sensor Networks,” Journal of Sensors, vol. 2013, no. 4,2013, pp. 572-575.
[45] C. Karlof, D. Wagner, “Secure routing in wireless sensor networks: attacks and countermeasures,”Ad Hoc Networks, vol. 1, no. 2–3, 2003, pp. 293-315.
Biographies
- China Communications的其它文章
- Service Function Chain in Small Satellite-Based Software De fined Satellite Networks
- Impact of Phase Noise on TDMS Based Calibration for Spaceborne Multi-Beam Antennas
- A Novel Roll Compensation Method for Two-Axis Transportable Satellite Antennas
- Coordinated Resource Allocation for Satellite-Terrestrial Coexistence Based on Radio Maps
- Heuristic Solutions of Virtual Network Embedding: A Survey
- Stochastic Dynamic Modeling of Rain Attenuation: A Survey

